Abraham Maslow was a humanistic psychologist, which put him in a different bucket than other psychologists you are probably familiar with. Unlike Freud, for example, who studied mental illness and emotional disorders, Maslow spent his time studying healthy and successful people.
As one of the most cited psychologists of all time, Maslow is perhaps most well known for his hierarchy of needs as well. This theory has implications for the cybersecurity industry, and we’ll be discussing that in this blog.
Maslow’s hierarchy of needs is a prioritized flow of human needs and motivations as they move through healthy human development. The idea is that it is significantly tougher to move higher up the pyramid toward full human potential without the basic needs of the lower levels being met to satisfaction.
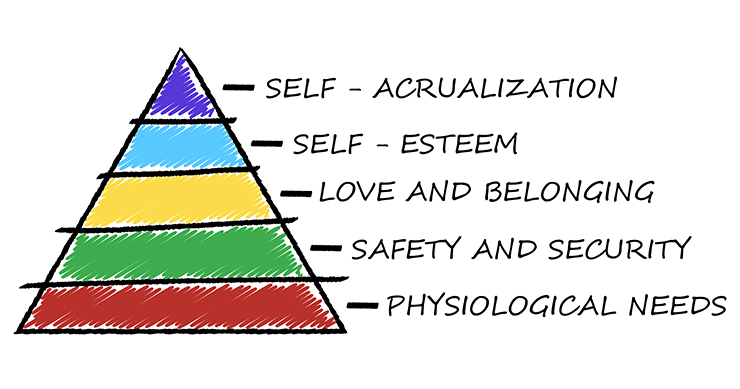
Maslow’s Hierarchy of Needs For Cyber Security
The original hierarchy of needs Maslow created nearly 80 years ago connects directly to the security landscape we know today. The value for security professionals in understanding the hierarchy of needs as they relate to cyber security can help them deeply understand the status of their IT systems and structure effective mitigation strategies for the risks that are inherent at each level. Ultimately, as they travel up the pyramid of cyber security hierarchy of needs, they will develop a resilient risk posture and effective incident response and recovery strategies.
Self-Awareness
At a very basic level, an individual must first be aware of who they are and be mindful of their own existence. Translated into security, we can refer to this stage as an awareness of who and what our IT systems are comprised of to form a general idea of who and what we’re trying to protect. If you don’t have a sound awareness of your system, you will most probably fail at responding to threats, and will certainly fail at responding to sophisticated attacks. Often, we see organizations jumping to buying “advanced” security solutions and services but would do well to first understand the nature of the “beast” they’re trying to protect.
Questions to Ask at This Level:
- What’s on the network?
- Is it supposed to be there?
- What’s installed on it?
- Who uses it?
- Who administers it?
- Is it configured securely?
These are critical questions because if you can’t accurately answer these questions, it becomes very hard to defend yourself.
Solutions that Address Needs at This Level:
- Asset tracking
- Patching systems
- Network access control
- Monitoring and log collection
As G.I. Jones taught us, “Knowing is half the battle.”
Basic Needs
Once an individual is aware of who they are, they can then focus on their physical needs for security, safety, and shelter. People crave a secure, safe environment. Therefore, they opt for things that will help to fulfill this in their day-to-day lives.
This is the stage where we see a lot of organizations start to build out their security posture with basic cybersecurity solutions like:
- Anti-malware solutions
- Firewalls
- EDRs
- Email security
- WIFI security
One often overlooked practice at this level is backups. Backups are more proactive than the above-listed items. It’s more exciting to take part in “active” defense strategies to protect our IT systems, but in truth, proactive security practices are equally, if not more, important. When organizations get hit with ransomware, the resources that are spent to get departments or entire organizations back to a normal operating level are alarming. Implementing a backup and logging system should be at the most basic level of security measures.
This level can be referred to as fundamental. Without fully covering this basic layer, it’s really hard to reach a strong security posture.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days
The Need for Belonging
With primary needs met, the next step on Maslow’s hierarchy of needs is love and a sense of belonging. People are social creatures, and the desire for friendship, intimacy, acceptance, and love comes naturally.
In terms of cyber security, love isn’t so relevant. But we can understand this as a need to hold on to the things that are most valuable to you as an individual or organization. This level is all about securing the crown jewels. When organizations get to this level of security, they’ll generally be looking at more high-level security strategies like data loss prevention solutions, multi-factor, and adaptive authentication solutions, as well as web application firewalls.
This level is arguably the whole point of cyber security and corresponds to the CIA triad: confidentiality, integrity, and availability. At this point on the pyramid, organizations are concerned about identifying and controlling the data that is most valuable and sensitive to their objectives.
Identifying and controlling data
- Where does our sensitive data live?
- Who can access it?
- Where is it allowed to go?
User monitoring and control
- Where do your users live in your environment?
- Where can they access your data?
- How do they access your data?
Applications need to be protected, too, at this layer
- Ensure that third-party apps are supported and patched by providers
- In-house applications have been thoroughly tested
Self-Actualization
The point on the pyramid is the desire for self-actualization to reach one’s potential. At this level, the pinnacle of the hierarchy is reached, although, in reality, it’s not quite possible to get there and just stay. No IT security system or human being, for that matter, is ever totally complete. But by adequately addressing all the underlying stages, it’s possible to reach resilience, even in the event of a threat being actualized.
At the level of security actualization, assets, data, and technology are all protected. This level focuses on people. Training should be required across all end users to administrators at regular intervals. Employees and stakeholders should be enabled to make good security decisions for themselves and the organizations. Admins need to understand what their roles are in incident response and avoid having too many cooks in the kitchen when having to rapidly respond to a threat.
At this level, your incident response strategy can be actualized to its fullest. This is where it all comes together.
Incident Response at the Top of the Pinnacle
As you can see, a comprehensive incident response strategy that shows strong posture and resilience is located at the very top of the pyramid. This is because it’s very hard to know how much detection and response you want to factor into your strategy without a solid foundational baseline guiding your direction.
For example, if you fail to designate a responsible party that focuses on the “fundamentals”, performing tasks such as patch management, resources to administer proxies, firewalls, and identities, it’s going to be a tall order to build an incident response strategy that will be effective. In most cases, if there aren’t sufficient identification and protective mechanisms in place, you cannot do detection and response.
Centralyes allows you to build a security program that orchestrates and automates your entire security lifecycle- from identification to incident response and recovery. Ultimately, we want to be sure that you have the competence, strategy, and manpower to stay resilient in the face of growing cyber threats. Centraleyes can help you get there.
Book a Demo Today!
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days





