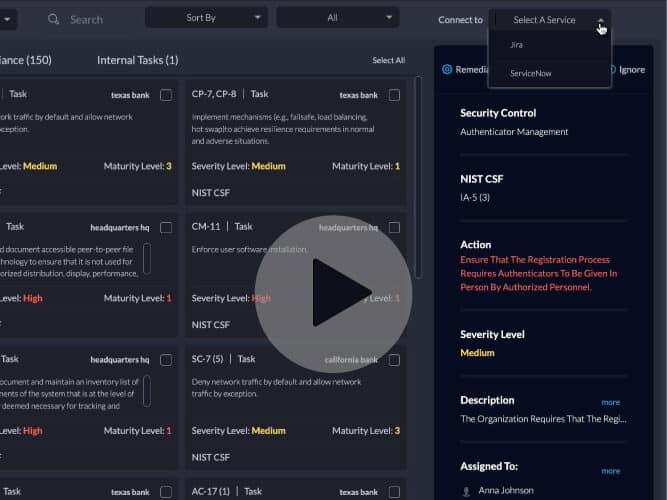
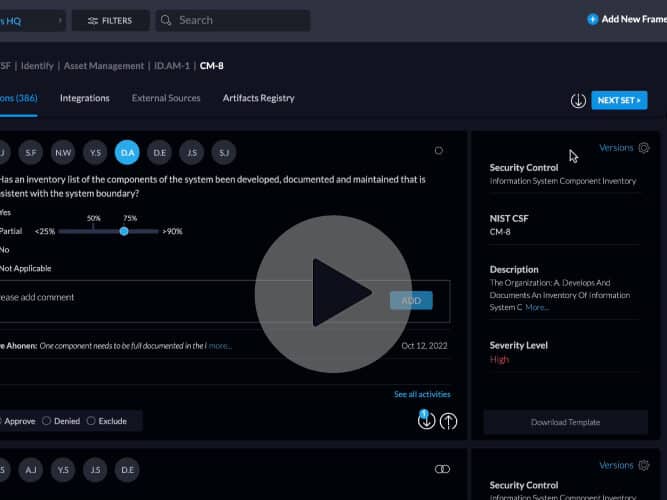
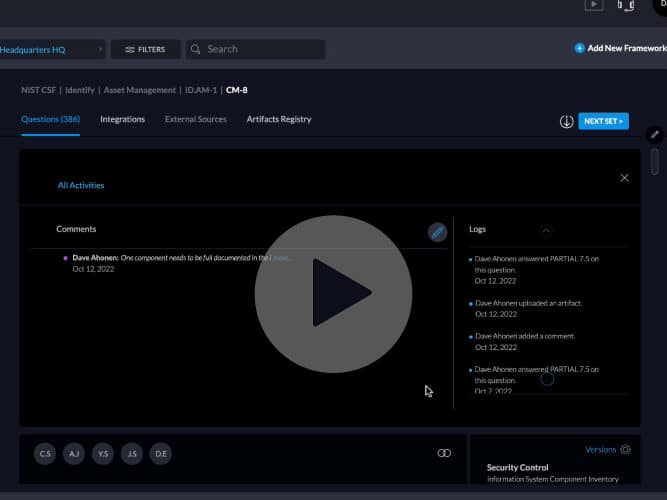
The Centraleyes platform offers a source of automated intelligence data feeds, which complements the self-attestation collection made by third party vendors. When you add a vendor to the platform, an automated live scanning starts on that vendor.
The scans look at their open source intelligence, attack surface, perimeter and footprint, on the public web, dark-net and deep web, as well as other sensitive data allocation tools to collect all available data. When you look at each vendor’s scan details you’ll be able to see a tremendous amount of information being collected and scanned in the platform, and automatically being correlated with their probability score on their risk assessment. You can see live information on active breaches, external threats, open ports, etc.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days
Aside from documenting this information, you can also create and push an action item for a vendor to deal with a gap with a click of a button.
Another exciting feature is that you can actually see 12 years of history on a vendor and view a report card with how many breaches that vendor has been involved in the past. The scans include things like domain ratings, SSL, TLS certificates, web application strengths, IP reputation, open ports, vulnerability scans, credential threats and theft, etc.