Vendor Risk Management
- Home
- Vendor Risk Management
Third Party Risk Management
Third party risk management (TPRM) is the management of the risks associated with the use of any outsourced processes, products or services. This includes the identification, assessment and mitigation of those risks. The goal of VRM is to allow organizations to take advantage of the benefits of working with third parties while ensuring the protection of their sensitive information and assets.



TPRM is a strategic approach to risk management that enables organizations to identify and address potential risks before they can have a serious impact. As organizations become increasingly reliant on outsourced suppliers and external vendors, vendor risk management has shifted from “nice to have” to “critically important.”
Third party vendor risk management is a tool that companies should be utilizing to ensure that their vendors adhere to relevant laws, regulations, and industry standards. Additionally, it helps with vendor selection, giving organizations the chance to choose based on the best quality and service for the lowest possible cost. TPRM proves to organizations that their suppliers are adequately protected and secured from cyber threats. Ultimately, if a comprehensive TPRM program is in place, organizations can be sure that their vendors are following the organization’s policies, processes, and procedures to protect their data, systems, and infrastructure.
Background to Third Party Risk Management
As organizations rely more and more on third-party vendors for goods, services and products, TPRM has become a critical component of a company’s overall risk management strategy.
In recent years, the supply chain has exploded with the rise of outsourcing, cloud computing and other vendor-dependent business models, driving many companies to outsource multiple business functions.
In the early 2000s, the world opened its eyes to the importance of managing vendor risk, after several leading companies were impacted by data breaches due to vulnerabilities in their third-party systems. People realized that vendors were not being properly managed and a number of regulations were introduced to mitigate this issue.

Organizations responded to these incidents by developing vendor risk management programs to properly identify, assess and mitigate third-party risks. Today, VRM is considered a best practice and is a requirement of many laws and regulations.
As companies become increasingly dependent on an ever-growing list of vendors, many of the earlier TPRM programs are now outdated, tedious and complicated. The new look is modern, sophisticated, all-in-one TPRM programs.

Vendor Risk, Third-Party, Supply Chain, what’s the difference?
There are many names for an organization’s outsourced processes and products. Are they all the same? Completely different? They are very similar with slight nuances:
Third-Party is the blanket term for all parties that supply services or goods to your company. Suppliers, service providers, vendors, and partners, all are included in this category.
A Vendor is a third party that supplies a service or product directly to you. Consequently, all vendors fall under the third-party category, but not all third parties are necessarily vendors.
The Supply Chain refers to the upstream and downstream of goods and services, the flow of it all. It may be made up of internal or outsourced entities.


The risks slightly differ for each of the above. Third-party risk management (TPRM) is the process of identifying and responding to any risk associated with third-party entities. Vendor risk management (VRM) focuses on risks related to vendor entities. Lastly, supply chain risk management (SCRM) prioritizes supply chain-related risks.
Why is third-party security so important?
Vendor security is a critical aspect of an organization’s overall risk management strategy. It helps ensure that the organization is not exposed to unnecessary risks when relying on external vendors for goods or services. The goal of a vendor risk management process is to protect the organization’s assets, reputation, and operations from potential threats or vulnerabilities that may arise from the use of external vendors.
Vendor risk management can not be optional. It would be a mistake to think, “if we have time after all our other requirements, then maybe then we’ll take a look at it.” It needs to be on the playing field right alongside your other top concerns. Vendor risk is just as important as every other critical risk your company is facing. Often, suppliers have almost as much control over your systems as you do. And they definitely have access to far too much of your information. Likely a lot more than you realize. A comprehensive risk management program to handle all vendors is the smartest pathway to keeping an eye on everything that’s happening with your organization’s information, whether inside or outsourced.
Apply Third Party Risk Management to your organization today
The Benefits of Third Party Risk Management
Third party risk management tools provide a number of benefits to organizations. These include:
Reduced risk
Proactively assessing and monitoring risk across all vendors promotes consistency and ensures that every vendor is meeting your business and security requirements, thus significantly reducing exposure to potential risks from vendors.
Improved compliance
A streamlined process to manage vendors ensures that all vendors are being monitored and helps confirm vendors’ compliance with required laws and regulations, while also keeping your organization compliant with regulations that mandate vendor risk management and reducing the risk of heavy fines and penalties.
Enhanced security
Overseeing all providers and understanding their risk posture gives your organization a clear picture of what needs improvement and where. A VRM program keeps track of vendors and ensures that they are constantly improving their security measures, essentially enhancing your organization’s security as well
Increased efficiency
A comprehensive VRM beats outdated spreadsheets by streamlining the processes and giving your company full visibility over your vendors’ security postures, allowing you to quickly identify and address potential problems.
Framework Profiles
Initially, integrating a VRM program will be costly, but after the preliminary overhead, it significantly reduces yearly expenses. This is in addition to the costs associated with no program at all, such as regulatory fines, data breaches, and reputational damages.
How to implement a third party risk management program?
Many companies are already aware of the importance of applying a vendor risk management process, and they’ve implemented some sort of program, yet it’s just not working effectively. The vendors are sent long-winded excel-based questionnaires and are forced to run between different departments to answer the various questions, chasing after evidence, policies, and documentation. Once the organization finally receives the assessments, a significant amount of time is usually spent determining if it was answered correctly and if all the necessary documentation has been received. Outdated risk management programs are confusing and labor intensive and put pressure on the relationships between different teams as they attempt to work together with an inefficient solution.
- A list of all third-party suppliers
- Risk Identification
- Assigning severity ratings to each vendor
- Vendor management over time
By taking a proactive approach to third party vendor risk management, organizations can better manage their risk profile and increase their overall security posture. The process begins by listing every single vendor. Yes. Including the small retail startup that sells the company customized swag once a year. They have the company’s credit info, do they not? Once the list is complete, identify the types of risks those vendors can pose, such as financial, operational, legal, and reputational risks. Organizations can then assess the impact of each risk and develop strategies to mitigate them.
Types of third party risks
Reputational Risk
When a third party suffers a data breach or gains other negative attention, this reflects badly on the organization and affects your own reputation
Financial Risk
This risk refers to the potential financial loss to an organization through their vendor, such as vendor bankruptcy, fraud, or mismanagement
Legal Risk
Legal issues arise when the vendor is dealing with legal problems such as violation of laws and infringement of intellectual property rights which exposes the organization to legal liability
Fourth Party Risk
Apply Third Party Risk Management to your organization today
How do you score third party risks?
At this stage of a third party management risk assessment, the organization should focus on determining the supplier’s risk posture. This includes discovering risks associated with the vendor, assessing their security controls, understanding the vendor’s business practices, and inquiring about their economic stability. The final results should be used to assign a score and severity rating for the provider.
A vendor cybersecurity questionnaire is recommended to accomplish this. The questionnaire results should provide you with clear, quantifiable information about the supplier’s security posture and help you determine if this vendor is a good fit for your organization.
A score should be assigned to the vendor based on the results of the cyber risk questionnaire and any other evaluators used. This score should be calculated using an established severity rating system chosen in advance. The organization can now determine whether the vendor is suitable for them and if there are specific risks that need to be managed. The scoring system allows organizations to quickly and accurately assess vendors to identify potential risks and develop plans to mitigate those risks. Additionally, this rating system can be used to assess vendors for the purpose of auditing and monitoring their performance.
Once the assessment is complete, the organization should develop a risk response plan. This plan should include strategies to respond to the risks posed by the vendor, such as mitigating, avoiding, or accepting the risks, implementing security measures, performing regular audits, and requiring specific certifications and qualifications. The response plan should also include procedures for terminating the relationship with the vendor, if necessary.
This is where continual risk management is critical. Having a one-and-done risk assessment is of no value as the risk landscape is constantly changing. The organization should create a continual vendor risk management plan including processes and procedures for managing the perceived risks. Roles and responsibilities should be assigned to relevant personnel ensuring that all the processes have owners. Audits, tests, and evaluations should be scheduled at least annually for all vendors (consider more often for higher-risk vendors) and risk assessments need to take place on a regular basis.
Third Party Risk Management Policy
An additional aspect of managing vendor risk is to develop a third party risk management policy. Policies are those fun sets of rules and standards that companies love to hate. There are so many policies to write, each slightly different than the next, dragging on and on. But they are an important piece to proving compliance, as most if not all compliance frameworks require many policies (and they will check for them during an audit). It also does have real value if written well!
The third party risk management policy should clearly define the organization’s expectations for its vendors, as well as the processes and procedures that will be used to evaluate them. It should also include processes for monitoring vendors and responding to risks that are identified.
The goal of the policy is to maintain an agreed level of security in your third-party relationships.

Vendor Monitoring
Once a vendor is onboarded, it does not mean the organization can ignore them. Every vendor should be under continuous monitoring. Monitoring gives companies the ability to keep tabs on their suppliers. The monitoring process should include frequent reviews of the vendor’s performance, as well as tracking changes in the vendor’s risk profile. A change in profile would indicate that a risk assessment needs to be conducted again to determine if the vendor is still at an appropriate severity level. Organizations should also review the vendor’s security and privacy policies, and other compliance requirements on a regular basis.
Supply Chain Risk Management Automation
VRM can be really time-consuming especially if you want to do it right and feel satisfied that you are effectively managing your vendors. There are new vendors being onboarded, new regulations, and a constantly shifting cyber world with new risks being discovered daily. An automated vendor risk management program is where it’s at, allowing you to easily keep track of your vendor risk while keeping your VRM relevant to the changing times. Automation ensures that vendors are onboarded in a smooth, fast and clean operation. It means easy scanning and tracking, clear risk information on every vendor and detailed reports. It allows you to step back with the knowledge that your vendors are in good hands.
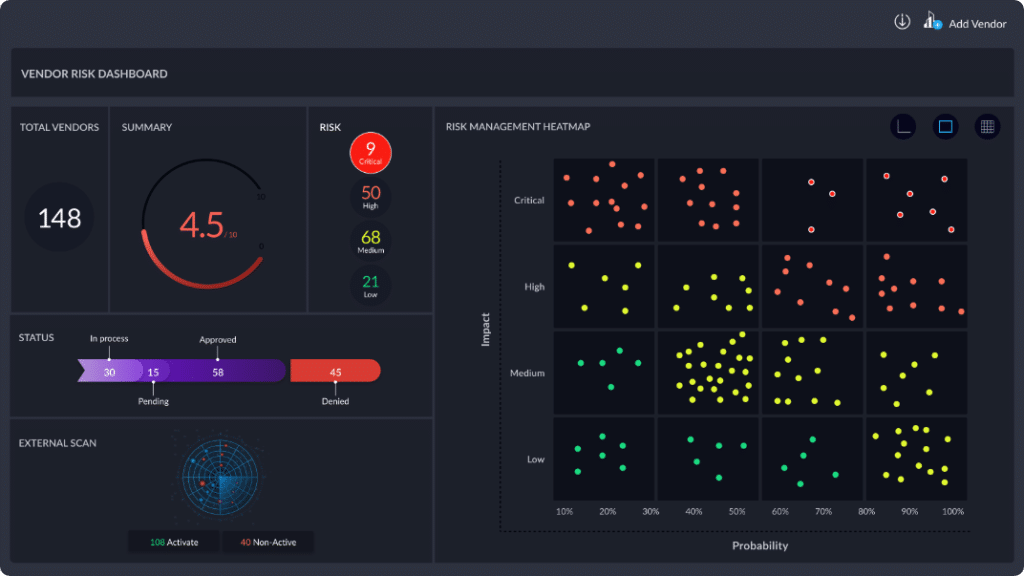
Using Centraleyes to Manage Your Third Party Risks
Centraleyes offers businesses a unique third party risk management tool, allowing companies to fully manage their third parties using a single platform to onboard new vendors, assess, categorize and prioritize them, continually monitor them, and view a comprehensive risk profile for every vendor with real-time remediation dashboards and downloadable reports. The platform shaves off hours of manual labor, allowing you to focus on the more pressing matters at hand with the knowledge that at least your vendor risks are no longer on that list.
The platform’s customized third-party dashboard uses a hybrid risk approach, to automatically
provide a clear view of the highest-risk vendors, with actionable guidance on how to mitigate gaps. With real-time threat intelligence and active scanning, you will feel secure in the knowledge that you have strong security practices in place to manage your third- (and fourth!) party risks.
Centraleyes will literally transform the way you work with your supply chain saving you immeasurable time, money and resources.
Join countless satisfied customers who are effortlessly managing hundreds of vendors as we speak.
See the platform’s third party risk management in action
Learn more about Third Party Risk Management
Fun Facts
TPRM is a continual process. The risk landscape is ever-changing, and organizations need to keep up with that by ensuring the continuous monitoring and observation of suppliers and tweaking the vendor risk management process as needed.
Third party risk management involves various assessments. Cybersecurity questionnaires, penetration tests, on-site assessments, and vulnerability assessments. With the final goal of determining the vendor’s overall risk to the organization.
Automation is key for proper TPRM. Using third party risk management tools that automate most of the manual processes including sending questionnaires, collecting responses, and generating reports, greatly reduces time and effort.
It’s not just the job of the security team to handle vendor risk. Stakeholders (top management, legal and financial teams, etc.) should be somewhat involved in the process, mainly to ensure that vendor risk management is aligned with the company’s overall risk strategy and goals.
Every single third party needs to be managed. This includes the small suppliers all the way up to the vendors that access sensitive information. Cloud service providers need to be considered as well as temporary staff.
Another aspect of vendor risk management is pre- and post-contractual assessments. A pre-contractual assessment is performed before contracting with a vendor, and a post-contractual assessment is conducted following a contract signing to ensure that the provider is meeting the organization’s requirements.
TPRM also helps with compliance and regulatory requirements. Managing vendors is a requirement for complying with many regulations and compliance frameworks such as GDPR, PCI-DSS, ISO 27001 and HIPAA.





