Compliance Automation
- Home
- Compliance Automation
Compliance Automation
The importance of compliance automation cannot be overstated. Implementing automation for compliance and auditing makes it easy and cost-effective to enforce policies, assess controls, and conduct ongoing monitoring and reporting. Given the not-so-gradual shifting trend towards increased compliance mandated by regulatory bodies and authorities across various sectors, the importance of automating compliance processes is taking priority more than ever.



In today’s complex web of regulatory demands, the processes and procedures that are associated with auditing and compliance simply cannot be sustained manually. Manual processes have proven to be fatigue-inducing, financially straining (or draining), time-consuming, and subject to human error.
For example, without automation, an organization may spend weeks at the end of a year detecting compliance violations and remediating them manually. Even then, there’s no assurance that every violation will be caught and properly addressed. By contrast, a data-driven, automated solution can instantly and accurately detect violations.
The cost and the level of expertise you need to have, the resources required and the management needed are just untenable otherwise. It’s virtually impossible to stay in compliance today without an infrastructure that supports automation.
Ongoing, continuous monitoring and verification are also critical. The companies you engage with don’t want to know that you were compliant, say, three months ago on the 15th of the month. They want to understand what controls were put in place in order to achieve your certification or pass your audit, but no less importantly, they want to gain insight into what has been and is continuing to be done every day since.v
Automation simplifies the full breadth of compliance and audit-related processes with:
- A combination of automated capabilities of data collection, violation alerts, regulatory updates, and reporting to streamline comprehensive audit and compliance workflows
- Automatic logging of processes to provide a complete, proven audit trail to review as needed. When put in the uncomfortable position of explaining to the CEO or to investors how the organization’s existing security infrastructure allowed hackers inside, audit trails provide sequential logging of the actions taken and the controls implemented, doing away with the feverish frenzy that accompanies finding the necessary documentation when time is short and pressure runs high.
- Automated risk assessments measure internal risk exposures, as well as third and even fourth-party risks. An automated platform gives you deep visibility into your corporate and vendor ecosystems, providing the information you need to make smart decisions about contractors and suppliers.
Apply Compliance Management to your organization today
The Evolution of Compliance
A company’s alignment with internal and external rules, laws, or standards is referred to as compliance. The purpose of these regulations may range from protecting sensitive data to ensuring data integrity and consumer privacy. We’ll outline a brief history of compliance as we know it today.
FCPA: 1977
Experts concur that the start of compliance as we know it today was a response to the financially scandalous era of the 1960s. Following that decade, a Securities and Exchange Commission (SEC) investigation found that hundreds of US companies, including some very well-known and reputable ones, bribed foreign officials in order to further their commercial interests. In response, the Foreign Corrupt Practices Act (FCPA) was passed.
The Sarbanes-Oxley Act of 2002
At the turn of the millennium, false accounting problems led to the bankruptcy filings of Enron and Worldcom. The two mammoth corporations were accused of manipulating their financial statements to inflate profits.
The Sarbanes-Oxley Act of 2002 (SOX) was created to provide investors with a number of safeguards against future fraud as a result of the erosion of investor confidence brought on by these activities.
The 2010 Dodd-Frank Wall Street Reform
The United States experienced a second financial crisis before the first decade of the new millennium was over. The 2010 Dodd-Frank Wall Street Reform and Consumer Protection Act (Dodd-Frank) was passed in response. Dodd-protection Frank’s of the US economy from financial institution collapses like those that occurred in 2007 and 2008 was one of its main objectives.
In the 2010s, a concerted effort to enforce compliance through public and commercial initiatives was highlighted. Businesses in the United States were now more aware of the benefits of compliance. In fact, companies without effective compliance processes risked being penalized with severe fines. With the aid of organizational and regulatory agency guidance, organizations were encouraged to identify risks and increase the likelihood of voluntary notification of breaches by developing and implementing compliance procedures.
From 2010 to 2023
The last few decades have ushered in an approach that considers not only traditional aspects of effective compliance programs, but combines them with risk management and social responsibilities, moving beyond the letter of the law or corporate policy and addressing compliance as a beneficial process that drives corporate value and trust.
Compliance remains a top priority for businesses today, and they are increasingly harnessing automated processes to monitor employees and increase the effectiveness of compliance programs. Data analytics help compliance teams identify patterns that human beings cannot recognize, improve the way risk is managed and respond quickly to developing compliance issues. Of course, data analytics are only as effective as the data inputs and analytical outputs, so although this technique is a useful tool, it is not a replacement for the human element so crucial in a compliance program.
Compliance Lessons From Covid
The pandemic era continued to teach companies important lessons in the field of compliance. Of the many lessons learned from the disorder so commonplace in those few disruptive years, one lesson was that the methods businesses were employing to deal with disruptive risks were antiquated. A major barrier was the overreliance on point-in-time evaluations for risk monitoring. Risk and compliance assessments were frequently only performed once a year or, at the most, after a significant cyber incident. This method’s static nature led to significant blind spots since the data it collected quickly became irrelevant in the constantly shifting risk environment. Effective risk mitigation and compliance, business leaders realized, required ongoing risk awareness and continuous monitoring.
Businesses all over the world are still looking for better ways to manage risk and compliance today and prefer automation over exclusively human, manual solutions.
Today’s challenge is to find better ways to leverage the massive amount of generated data for increased business resilience and disruption avoidance in addition to managing compliance in a cost-efficient and
time-effective manner.

What Is Compliance Automation?
Compliance automation is the term used to describe the streamlining of compliance procedures via the use of software applications that make use
of technology to gather data and provide actionable guidance for
regulatory requirements.
By employing compliance automation software, organizations can more easily comply with regulatory obligations and reduce the risk of non-compliance.
- Continuously monitoring data access
- Generating visual metrics and reports
- Scheduling audit tasks
- Alerting relevant parties when violations are noticed
How Does Compliance Automation Differ From Traditional Compliance?
Automated Gap Remediation
An automated compliance system enables you to easily analyze compliance gaps. Once the gaps are identified, the platform will create automated actionable remediation tasks, guiding the team on what they need to do.
The Centraleyes platform’s proprietary ticketing system tags a severity level to each action, enabling smart prioritization and management of those tasks, and allowing you to run different workflows, such as remediate, accept, assign, or ignore.
The platform is fully integrated with ITSM systems such as JIRA and ServiceNow, which allow for both pushing data out to those platforms and pulling back updates so that you’re always up to date.

Visibility
For larger organizations, manual monitoring is no longer sufficient. Through automation, compliance and security teams can achieve a complete view of their entire ecosystem, from internal servers to supply chain partners.
Automation of compliance is useful for increasing awareness of a company’s compliance status. Adopting an automated compliance system means everyone is on the same page and there is more transparency with compliance management concentrated in one centralized repository. It is simple for everyone in the organization to monitor and track progress because there is one single source
of truth.
An increase in visibility helps identify potential problems quickly before they develop into major concerns. Additionally, communication between various departments and personnel is enhanced via compliance automation technologies.
Full visibility means control.
- Stay in control with smart surveys, live data feeds, external threat intelligence, and quantifiable real-time metrics
- Identify gaps and inconsistencies with complete visibility via a cutting-edge centralized visual dashboard
- Unparalleled insight into your risk and compliance levels, set target scores and utilize actionable outputs
Aggregating Data in a Centralized Location
One of the challenges facing compliance management teams is the sheer amount of data points for data collection and establishing control. But when having all the data aggregated in a single platform you now sit on a gold mine of insights, which can strategically navigate you to focus on the most critical elements of your organization.
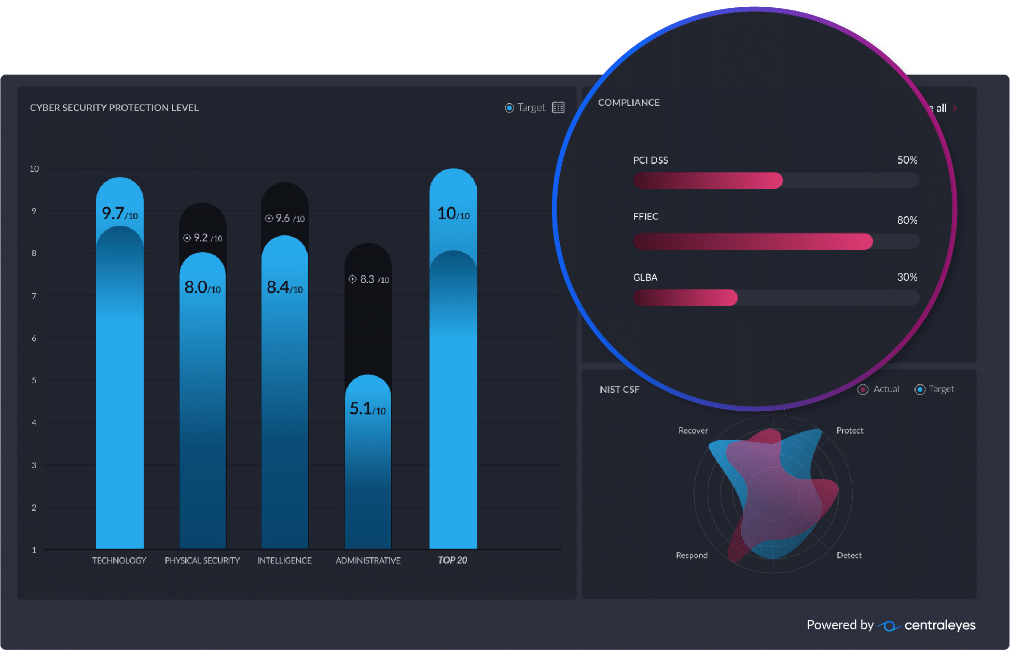
Centraleyes automatically gives you the ability to break down your risk score into various domains, such as technology, physical security, administrative, etc.
Through this lens, a new world of information opens up to you, allowing you to identify weaker domains, giving you the ability to compare your current status vs. your target, as well as the ability to track progress across all these domains over time, all at the click of a button!
Continuous Compliance Monitoring
As thorough as the spreadsheet or checklist of a traditional compliance check may be, it only captures a single point in time. Automated compliance platforms
scan for vulnerabilities, notify you of changes to security frameworks and offer
risk remediation guidance based on real-time data.
Risk Assessment as a Foundation for Compliance Management
- Largely manual, time-consuming work
- Captures a single point in time
- Inconsistent, and prone to human error and other regulatory compliance risks
- Little or no visibility of existing data or information
- Disjointed activities due to siloed processes result in high costs, inability to address third-party risks, lack of visibility into potential and actual risks, and difficulty measuring risk-adjusted performance
Potential Benefits of Automation
- Global visibility and more efficient use of resources
- Greater compliance with commitments met in a timely and accurate manner
- Enhanced speed through real-time storing, routing, capture & recording
- Continuous assessments and control monitoring
What Compliance Challenges Relate to Vendor-risk?
The enormous number of vendors companies engage with is one of the major compliance issues businesses must deal with. Numerous parties and data sources are frequently handled manually, which further drives up expenses. Since not all data is always readily and publically accessible, compliance teams frequently need to run after third-party vendors directly in order to gather first-hand information. This then introduces time-consuming, difficult processes. Business reputation suffers when onboarding processes and periodic reviews are not timely, which has a negative effect on the brand or business itself. Therefore, it is essential for company operations to be straightforward and efficient in order for customers to be able to update their data in a timely way whilst adhering to company-established processes.
The vendor onboarding process can be time-consuming and expensive, and it can put a strain on funding allotments and human resources. Employees may need to put in a lot of hours, particularly if the company works hard to have detailed compliance reports in order to abide by rules and regulations.
What is the Problem with Spreadsheets?
First of all, spreadsheets involve a process of manual input for both raw data and its relevant processing functions. Needless to say, manual operations are very fertile ground for data inconsistencies.
Secondly, spreadsheets mix data and calculation functions in a dangerous concoction. Anybody who has minimal background in spreadsheet functions knows from experience how easy it is to overwrite a function and replace it with a numeric value. Typing one word in a cell can erase a complex formula that may have taken hours to write.
With a database system, on the other hand, raw data and the execution of functions are two separate areas. As a matter of fact, end users are never allowed to directly touch the database, making it highly unlikely for data to be corrupted. The functions are done by the application and pre-programmed so there is no risk of human error getting introduced unknowingly.
Meeting Challenges Through Technology and Automation
The emergence of automated platforms like Centraleyes has created opportunities for organizations to tackle vendor risk and other significant challenges. With the introduction of these technologies, organizations can enhance efficiency in terms of both speed and cost reduction while fulfilling legal and security-related obligations, and building a positive brand image.
Automated technologies can help reduce the amount of time required by full-time employees to perform compliance tasks. This can provide various advantages to the organization and shift the onus of vendor assessments from tedious data collection processes into more of an analytical role to decide whether to onboard a vendor or not depending on the calculated risk score.
Document collection, which is fundamental for due diligence processes as well as data collection from various sources, can also be automated. This information can be provided in the form of a central report, which can also include an overall scoring of which level of risk is involved with onboarding the client or business. This can serve as material for human analysis.
With automation in place, supply chain and vendor-risk scoring is no longer biased by human judgment but rather extrapolated by a company-defined or legally-mandated set of rules. The indispensable role of human talent can instead be allocated to analyze the assessment results to determine whether to go forward with vendor onboarding or not, based on real-time information. With such systems in place, employees can dedicate their valuable time to work that provides better value to the organization.
Automation has become a crucial success factor. Businesses can optimize both back-end and front-end business operations, reduce the number of manual tasks, and focus on what matters most: precise and proactive security.
Components of Compliance Automation with Centraleyes
Centraleyes is the world’s most advanced integrated risk management platform and makes compliance simpler than ever with compliance automation. These are just some of the things we offer.
- More than fifty pre-loaded industry and regulatory frameworks and standards
- Streamlined data collection
- Automated scoring and tiering
- Smart mapping between systems.
- An intuitive dashboard
- Cutting-edge visualization and reporting for both stakeholders and compliance officers
- Single-click deployment for easy vendor management
- Guided vulnerability remediation
Risk-Based Compliance Automation

Compliance and risk management are interdependent terms. However,
too many organizations continue to view them as separate workflows
and departments.
Automation may help to bridge the gap between risk management and compliance by providing real-time insights into your compliance and risk management picture. If remediation is performed in order to satisfy new compliance criteria, the risk management team will gain.
The risk management team will then have a better understanding of the risks that are intrinsic to your business goals, implement controls to satisfy compliance requirements, and keep an eye on residual risks to determine whether further adjustments are required.

Robust risk management is nearly impossible without a continuous control monitoring system that uses automated tools. Using automation, organizations can identify when the system is not up to par to meet security and privacy standards. It can then react appropriately to remediate the security concern. Continuous monitoring identifies hidden system components, misconfigurations, vulnerabilities, and unauthorized actions. The provision of data-driven updates enhances a culture of proactive risk management.
Imagine a system in which risk-related actions are pre-programmed in accordance with the particular needs of the company, such as risk appetite, risk tolerance, risk thresholds, and risk scores. Once automated processes have processed and validated the data, the system can automatically assign the required risk actions to the pertinent internal or external resources.
Apply Compliance Management to your organization today
What Are the Benefits of Automating Compliance?
Cost-Saving
Organizations can save money by streamlining compliance-related procedures with compliance automation. No insult to our readers, but thanks to technological breakthroughs, humans are no longer the best-qualified species capable of successfully performing compliance tasks. As a matter of fact, automation actually reduces compliance headaches significantly.
Automated software is an investment, but in the long run, is less expensive than hiring numerous staff to manage procedures manually. Having said that, compliance automation does not eliminate the necessity of human presence in your compliance workflows, and compliance officers are still an absolutely essential aspect in achieving and maintaining compliance.
An additional point of cost-saving is that for many small-to-medium-sized enterprises (SMEs), adopting automated software to oversee most of their compliance workflows will help them avoid heavy fines and penalties by reducing the chances of human error.
Time-Saving
Organizations manage massive amounts of data. Handling all the data associated with your company manually would require a tremendous amount of labor, and modern technology eliminates this. Teams can do away with manual data entry, collecting, organizing, and searching thanks to systems that upload and sort information automatically.
Active supervision of repetitive and notoriously time-consuming compliance operations was required by the traditional compliance model. One of the major advantages of modern compliance automation is that it makes employees more productive by easing and supporting their workload.
Automation lessens the need to carry out laborious information-gathering procedures that can take time away from core business tasks. With automation, compliance teams have more time to install patches, strengthen security protocols proactively, and speed up audit workflows.
With an automated system, you may schedule repeating activities that will always be completed precisely and effectively. With human error almost entirely eliminated, security teams can concentrate on more valuable tasks.
Data Collection and Audit Preparation
Automating compliance-related tasks improve data collection and audit preparation in several ways. First, it helps ensure data is collected consistently and accurately. Admins can configure automated systems to collect specific data types and flag errors or irregularities.
Data automation also helps the process of preparing for an audit. This is because automated systems readily generate reports and analyses based on the collected data, saving time that would otherwise be spent manually analyzing the records and calculating conclusions.
Automating data collection improves the quality of the information provided to auditors. Automated systems generate accurate and up-to-date reports, providing a holistic view of an organization’s compliance and security posture.
Compliance automation systems keep a consistent log of processes. This log provides a complete, proven audit trail to review as needed. When put in the uncomfortable position of explaining to a CEO or to investors how a particular system or organization’s existing security infrastructure allowed hackers inside, audit trails document a complete listing of the actions taken and the controls implemented, doing away with the feverish frenzy that accompanies finding the necessary documentation when time is short and pressure runs high.
Automated Vendor Onboarding and Risk Profiling
Our platform lets you onboard a new vendor in as little as 15 seconds! This is possible thanks to our smart questionnaires and automated workflow functionality that allow you to customize a dedicated vendor assessment on the fly.
The vendors will begin their assessment within minutes through an intuitive user-friendly interface, that both helps guide the vendors to providing the necessary information, as well as automatically assists the vendor in mitigating critical gaps through our AI-powered remediation planner.
When conducting vendor risk management it is important to create a risk profile on each and every vendor in order to allow you to identify the highest-risk vendors in your organization.
Centraleyes automatically creates a vendor risk profile by quantifying the impact and the probability of an attack on a vendor, using a combination of internal categorization, vendor self-attestation, certifications, and other supporting documents. In parallel, it conducts automated threat intelligence scanning of the vendors’ internet-facing risk surface, which includes unprotected assets, ongoing and previous attacks, and breaches, along with a variety of other key data points.
Using this hybrid vendor risk profiling approach, we create the most accurate vendor risk segmentation for our customers’ third parties, helping them lower their third-party risk exposure with an easy click of a button!
Security
Compliance automation strengthens your cyber security posture in many ways.
- helps ensure systems and data are adequately protected by identifying and correcting security gaps
- monitors for unusual activity that might lead to or indicate a security breach. It also generates reports that can be used to assess an organization’s data security
- Keeps you updated on threat intelligence, zero-day vulnerabilities, and critical security alerts
- Alerts users of recent upd
Improved Communication
Compliance officers have a difficult time keeping track of work across teams and communicating with them. in particular, if they wish to maintain organization between emails, notes, and reminders. Risk managers may quickly allocate duties, track all work completed, and communicate with internal teams when using a single automated platform.
We Sync Compliance with Risk Management
An automated risk and compliance management solution weaves risk management into the fabric of an organization and enables a “risk culture” that facilitates a more agile, forward-thinking process that beats the outdated isolated compliance approach to security any day.
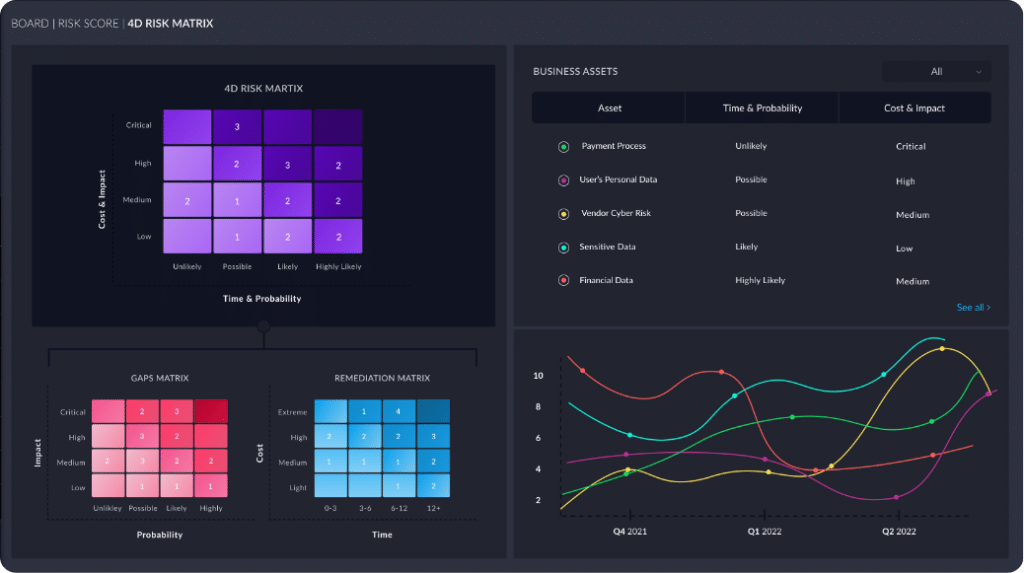
Real-time Insight and Reporting
Automation simplifies data analysis and reporting by allowing you to automatically create reports that show measurable progress. Save hundreds of hours by automating the collection and analysis of technical risk through our cutting-edge, visual dashboard.
With a platform like Centraleyes, you can understand your risk posture in real-time, track progress, and minimize your exposure to risk with automatically generated remediation steps and insights.
- create customized reports based on the data you collect through your risk assessments and ongoing remediation efforts
- Ensure cybersecurity investments are continuously improving with deep insights into current and historical performance
- Gain full visibility into the exact actions your organization is taking to improve security and compliance
Evidence Collection
One of the biggest difficulties a business facing an audit would undoubtedly confront is producing enough evidence. The controls that are required for the audit are often already in place in a lot of organizations. However, they fail to provide and preserve the proof that would be required to convince an auditor that the control was carried out. Especially in the case of SMBs and startups, there simply isn’t enough awareness and no pressing need to develop and maintain this documentation until the compliance auditing process is looming.
While managing the process manually with spreadsheets and following up through email is possible, Centraleyes offers a better way to navigate the compliance maze and audit your work as you do it. Technology makes a huge difference in audit evidence collection and management, facilitating tasks like storing documentation, creating forms, and following up on third-party risk assessments.
By automating compliance to enable audit trails and address overlapping regulations with other frameworks, you’ll simply eliminate the issues that accompany compliance done the conventional way—via manual screenshots, excel spreadsheets, and long meetings.

Quick Deployment
When it comes to installation, our cloud-based installation helps in rapid deployment so that you can get up and running real quick! With our no-code deployment, you’ll be onboarding and implementing in less than a day!
Where Do Humans Fit into All This?
It’s important to understand that although automation can make a business’s compliance efforts considerably more efficient, it cannot completely replace human oversight. Nor should it, Compliance officers are still necessary for any entity operating in a regulated sector. Automation covers the manual collection and evaluation processes, yet manual questionnaires still do exist and will continue to for the foreseeable future. Compliance officers are needed for these remaining manual tasks. They are also still required to oversee, and proactively use the analytics and reports to communicate with the executive level and build a compliance culture in a company.