When the guys at the National Institute of Standards and Technology (NIST) released the inaugural Cybersecurity Framework in February 2014, it did not include a batch of questions that were almost certainly on their minds but not in the framework.
- Would the framework become another entry on a long list of excellent–but unused–cybersecurity reference documents collecting dust on the digital shelf?
- Would the critical infrastructure industry embrace it?
- Which other sectors would find it relevant?
The answer came quicker and different than they expected: the “Framework for Improving Critical Infrastructure Cybersecurity,” as it was known then, moved well beyond the industry gates of critical infrastructure. It became the go-to framework for cybersecurity planning. But even in those first few months, no one could have predicted that it would be translated into over a dozen languages.
The original NIST CSF was aimed at critical infrastructure like hospitals and power plants. However, it gained extreme popularity worldwide in manifold industries of all types, stripes, and sizes. Although not intended for this vast audience, it is arguably the world’s most widely adopted cybersecurity framework!
As technological advancements and upheavals reached every corner of the industry, an update to the framework was sorely needed. 2014 was a long time ago in “cyber time.”
After extensive consultation with industry experts, academics, civil society leaders, and global partners, NIST released Version 2.0 of the CSF. The official NIST CSF 2.0 release date was Feb. 26, 2024. The new NIST Cybersecurity Framework 2.0 reflects its wide adoption and tailors the updated framework to a broader range of industries and levels. It is also aligned with the cybersecurity landscape as it looks today.
The CSF 2.0 is forward-looking and intended to apply for years to come as technology advances, specifically in these areas:
Kevin Stine, chief of NIST’s Applied Cybersecurity Division, said, “Developed by working closely with stakeholders and reflecting the most recent cybersecurity challenges and management practices, this update aims to make the framework even more relevant to a wider swath of users in the United States and abroad.”
After years of aggregating that feedback and public commentary and structuring it into a framework, one thing is clear: Industries across the globe largely supported the need for these changes.
NIST CSF 2.0 Changes and Updates
Let’s discuss the updates and differences between the NIST CSF 1.1 vs. 2.0.
This One is for Everyone
From the smallest educational facility to mega-corporations, the new edition is designed for all. Smaller businesses now receive a roadmap customized to meet their needs. Version 2.0 is no longer targeted to the major players. It’s simpler for everyone to improve their cybersecurity skills with real-world examples and a new web tool that links to other standards. This might truly level the playing field and strengthen the industry’s defenses against cyberattacks.
Now, There Are Six
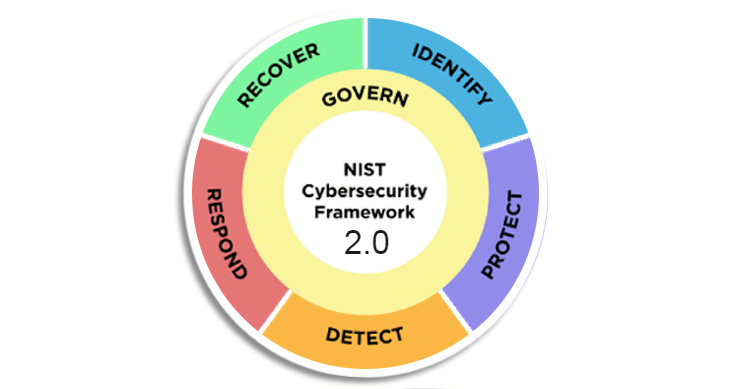
The core now comprises six functions—the previous version depicted five functions in the familiar NIST wheel. Govern is the newest of the NIST core functions: identify, protect, detect, respond, recover, and govern. Govern takes the center of the wheel now, as it informs how an organization will implement the other five functions. Combining all these functions provides an excellent view of managing the life cycle of cybersecurity risks.
Overview of the Six NIST CSF Functions
GOVERN (GV): The organization has a defined, shared, and closely watched cybersecurity risk management strategy. The outcomes of the GOVERN Function can be used to prioritize and accomplish the goals of the other five Functions. Integrating cybersecurity into an organization’s larger enterprise risk management (ERM) strategy requires effective governance practices.
The addition of governance aligns with many of the more recent laws and regulations, such the Europe’s DORA and the SEC’s Cybersecurity Rule, which seek to hold companies more accountable for cybersecurity and require transparency in the case of a serious cyber incident.
According to NIST, the governance function encompasses the following areas: roles, duties, and authority; policy; oversight of cybersecurity strategy; and understanding of organizational context, cybersecurity strategy, and cybersecurity supply chain risk management.
IDENTIFY (ID)—Understanding and identifying the organization’s digital assets (including vendors) allows an enterprise to arrange its priorities per its risk mitigation plan and the GOVERN-identified mission requirements.
This Function also entails identifying possibilities for improvement for the organization’s plans, policies, processes, procedures, and practices that support cybersecurity risk management.
PROTECT (PR) – The PROTECT function facilitates the capacity to safeguard assets to avoid or reduce the possibility and impact of unfavorable cybersecurity events.
This function covers the following outcomes:
- platform security (i.e., safeguarding the hardware, software, and services of physical and virtual platforms)
- awareness and training
- data security
- identity management
- authentication
- access control
- resilience of technology infrastructure
DETECT (DE)— With DETECT, abnormalities, gaps, and other potentially harmful occurrences that could point to potential or actual cybersecurity incidents can be quickly found and analyzed. This function supports activities for effective incident response and recovery.
RESPOND (RS)—This function observes and handles reactions to cybersecurity incidents.
This function’s outcomes include reporting, communication, analysis, mitigation, and incident management.
RECOVER (RC)— Operations and assets are resumed following a cybersecurity event under this function. To lessen the negative effects of cybersecurity events and facilitate appropriate communication during recovery efforts, RECOVER facilitates the prompt restoration of normal operations.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days
More Roads Lead to NIST
In the new version, NIST created a suite of resources to help all organizations achieve their security goals. The latest update features quick-start guides for targeted audiences and a searchable catalog for cross-references to other cybersecurity frameworks and documentation.
Also, the update includes implementation examples to guide newcomers through the ranks of the NIST CSF.
These guidelines were designed to provide a tailor-made path for various organizations into the CSF functions and smooth the road to implementation.
“The CSF has been a vital tool for many organizations, helping them anticipate and deal with cybersecurity threats,” said Under Secretary of Commerce for Standards and Technology and NIST Director Laurie E. Locascio. “CSF 2.0, which builds on previous versions, is not just about one document. It is about a suite of resources that can be customized and used individually or in combination over time as an organization’s cybersecurity needs change and its capabilities evolve.”
Quick Start Guides
New users can now learn from others’ successes and select their area of interest from a newly compiled set of case studies and easily navigable manuals designed for particular user categories, such as small businesses, corporate risk managers, and organizations looking to strengthen their supply chains.
Searchable Catalog
The new CSF 2.0 Reference Tool offers an intuitive interface for reading, finding, and exporting data and details from the CSF’s core. Users can browse and export sections of the Core by utilizing specific search phrases.
Specific filtering options like Informative References allow customers to customize the CSF 2.0 Core to suit their needs.
Information is presented by this tool in formats that are simple enough for both computers and humans to grasp.
Supply Chain Risks
Today, technology is supported by a complex, distributed global supply chain. Supply chain risk management is now a critical practice for all organizations. The guidelines in the CSF C-SCRM category (GV.SC) were included to address the heightened risk posed by expanded supply chains.
The supply chain guidance aligns smoothly with the National Cybersecurity Strategy’s emphasis on mitigating risk in supply chains.
Alignment with Other Frameworks
Many feedback responses also strongly endorsed the need for a new NIST CSF to coordinate with newly released NIST privacy standards or ERM solutions.
The NIST CSF 2.0 is compatible with the NIST Privacy Framework, NIST AI Risk Management Framework, NIST SP 800-53, ISO 27001, and CIS Controls, among other industry standards. This connection allows organizations to use current best practices, prevent duplication, and synchronize their cybersecurity activities. Informative references illustrate the relationship between the CSF and other cybersecurity frameworks, standards, recommendations, and resources.
NIST 2.0 Compliance with Centraleyes
Centraleyes has you covered as you embark on your journey to NIST CSF 2.0 compliance. Our data-centric security approach integrates comprehensive data discovery, advanced data classification, and robust risk management functionalities. Gain insights into your data’s whereabouts, sensitivity levels, and user access patterns to ensure compliance with NIST cybersecurity guidelines.
Centraleyes empowers organizations to proactively address cybersecurity challenges, ensuring compliance with NIST frameworks and enhancing overall resilience.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days






