A cyber risk analysis will involve looking at each and every cyber security related risk in detail, reviewing them as part of a larger cyber risk assessment process. An organization’s cybersecurity program must decide where to allocate resources and which risks to prioritize for mitigation. By undertaking a cybersecurity analysis, a company can build a clear picture of the risks facing their networks and systems, and begin to make strategic decisions and plans.
The ultimate goal of the analysis is to reduce risk exposure to acceptable levels, where it can’t be fully mitigated. More specific goals include:
- Identify specific project risks for awareness
- Prepare an incident response plan, once you have identified what could happen and how it will affect the business
- Anticipate adverse outcomes and put security in place to avoid them.
A cybersecurity risk analysis will include both a network security risk analysis and an information security risk analysis. These two specific elements are critical to analyze to identify the most important assets vulnerable to attack or compromise.
The two main types of cyber risk analysis are:
- Quantitative risk analysis
Perfect for determining costs or time, a quantitative analysis will numerically estimate the effect a risk will have against a given business objective. This can be done with the modern risk register.
- Qualitative risk analysis
This type of analysis measures the likelihood and impact of a particular risk. Understanding the chances of a risk event taking place and the significance it will have on a company, enables a company to prioritize which risks to deal with first. A risk analysis matrix will give you visibility into the results. An example of a simple risk assessment matrix is:
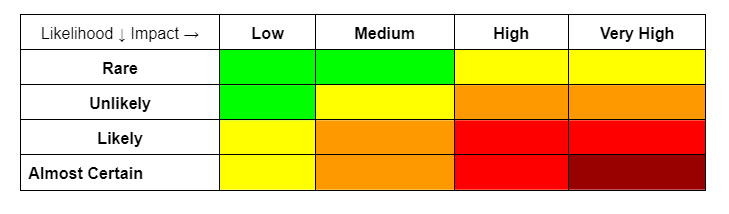
The various colors in a risk matrix will represent the varying levels of severity- a combination of the likelihood and probability, and can be numerically assigned to arrange prioritization. The risk matrix has come under criticism for not being detailed enough yet risk managers know that it is an extremely useful tool; it still portrays a clear graphical representation of risk posture, gives a quick and relatively inexpensive risk analysis, and enables you to decide which areas need more focus for a detailed analysis.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days
Risk analysis automation is a ground-breaking addition to the risk assessment process. As risks are identified, they are automatically entered into the risk register list and assigned their risk matrix positions. They can then be assigned financial values, sorted by probability or impact, and prioritized according to urgency. [The Centraleyes automated risk register is the first of its kind to do all of the above as well as suggest remediation steps and track mitigation.]
Using established frameworks for the risk analysis ensures you have covered every possibility and relevant topic for your industry. The two broadest frameworks to use are:
- NIST CSF– The NIST Cybersecurity Framework, guidelines and recommendations that take industry standards and best practices and combine them into a framework to enable organizations to manage their cyber risks.
- ISO 27000– A series of standards providing a worldwide relevant framework for information security management best practice.
Each of these provide an exhaustive list to ensure a full life-cycle approach to relevant risks, which can then be analyzed.
Steps Around the Cyber Risk Analysis Process
- Assigning a team to the project. Useful members include your CISO, Senior Management, stakeholders, managers and members of different departments.
- Take inventory of your assets- hardware, software, any machinery and more.
- Map your networks and systems- interconnections, firewalls, flow of information and more.
- Identify threats and vulnerabilities, through scanning, risk management software, review of security controls and patch management posture.
- Scrutinize risks and draw up a list. A risk register is a hugely useful tool for this.
- Using your list, perform your analysis on each one to determine its effect on your business’s reputation, finances, continuity, and operations.
- Implement solutions to mitigate or remediate risks and reduce exposure.
- Continue to monitor the status of the risks and keep any changes in mind that may affect the status of the solution you have implemented.
Benefits of the Cyber Risk Analysis
Undertaking a cyber risk analysis will:
- Save you money in the long run. Prepare for threats and attacks before they happen and preempt business continuity and a robust incident response plan.
- Increase organizational knowledge. You’ll get to know the entire structure and ins and outs of your company.
- Create a template for future assessments. As a continuous process, this is key to maintaining a constantly diminished risk exposure.
- Possibly the most important benefit: Prevent data breaches, threats and attacks from actually causing you damage!
- Increase compliance and decrease regulatory fines.
Undertaking a cyber risk analysis for your company may seem overwhelming but it is absolutely achievable using the right tools. Centraleyes risk and compliance management platform will ease each step via automated risk registers, remediation suggestions and customized reporting and progress tracking. Watch a demo to see how it can help you.
Start Getting Value With
Centraleyes for Free
See for yourself how the Centraleyes platform exceeds anything an old GRC
system does and eliminates the need for manual processes and spreadsheets
to give you immediate value and run a full risk assessment in less than 30 days





