Mourne Fourie
Mourne Fourie
7 Steps to Accelerate Your Cyber Risk Remediation Initiative
The digitization of the modern workplace has emphasized the importance of cybersecurity for businesses everywhere. Cyber threats…
Cyber Leaders of the World: Rob Black, CEO and Founder of Fractional CISO
Please tell us a bit about yourself, your background, and how you got into the cybersecurity industry.…
The Problem With Heat Maps
Some of you are likely inclined to dismiss that idea outright. Traditionally, organizations that use a heat…
Continuous Control Monitoring: Why is it So Important?
Security teams are tasked with the job of assuring that business risks are securely managed and that…
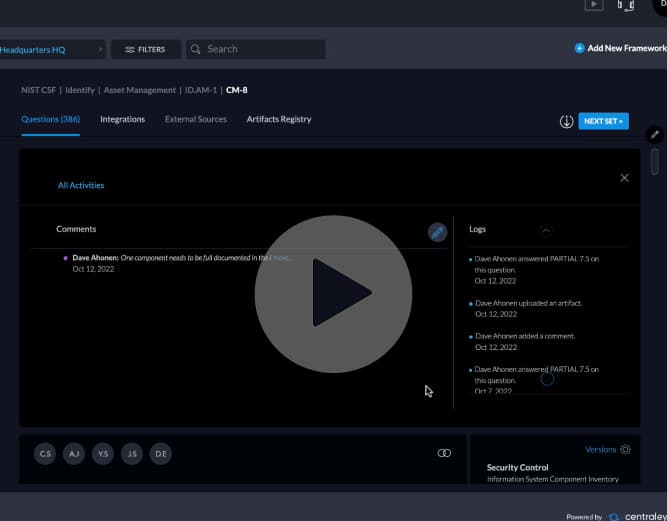
Stay in the Know With a Full Activity Log of Your Assessment Collection
The Centraleyes platform offers a full audit trail of all of the activities contained within your assessments,…
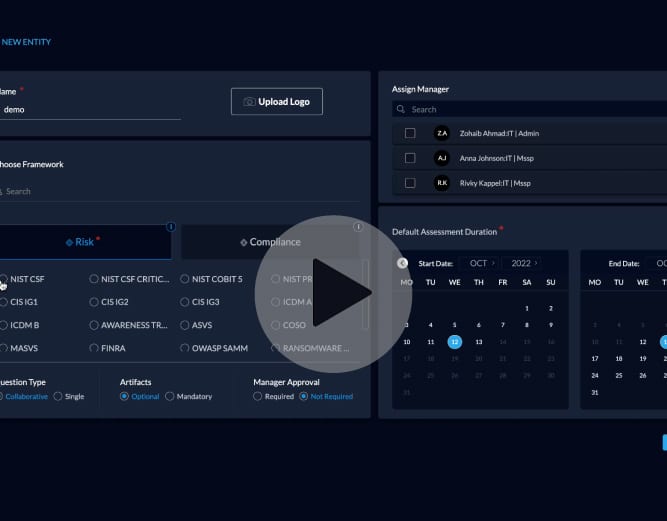
Add a New Entity to Perform Your Assessment in 10 Seconds
Creating a new entity in the Centraleyes Multi-Entity 1st Party module provides you with another layer of…
Struggling to Fix Cyber Governance? Here Are the Most Powerful Strategies
Definition of Cyber Governance Cyber security governance provides a strategic view of how an organization controls its…
Pros and Cons of Continuous Compliance Solutions
Compliance Audit Woes Compliance audits are STRESSFUL. IT teams work overtime and overnight to collect evidence of…
Cloud Compliance: Best Practices for Success
Race to the Cloud Cloud migration is not just a quick shift from traditional network systems to…
Guide to Cloud Security Risk Management
Cloud computing is transforming enterprises and e-commerce markets globally, thanks to its scalability and flexible usage. Within…
Cyber Risk Quantification
If there’s one thing that’s certain in the expanding digital world, it’s that nothing is certain. Unseen…
Risk Quantification: Why Quantifying Is Only the First Step to Effective Risk Management
Breaches have never been more expensive. Don’t believe us? See for yourself. The average data breach cost…
The Difference Between Due Diligence and Due Care in Cybersecurity
Due diligence and due care are commonly used interchangeably, but in the world of cybersecurity, they have…
Cyber Leaders of the World: Zachary Lewis, CISO at the University of Health Sciences and Pharmacy in St. Louis
Please tell us a bit about yourself, your background, and your journey of becoming a CISO for…
The Ongoing Need for Cyber Insurance
Cyber Insurance is not a new concept — it has existed in one form or another since…
Managing 4th Party Risk in Your Enterprise: A Step by Step Guide
Supply chains have never been more complex and intertwined. The result is a network of vendors and…
How to Stay Secure and Compliant in a World of Regulatory turmoil
Watch this special, collaborated webinar session where industry experts from Netsurit and Centraleyes meet at an intriguing…
Centraleyes Announces the Addition of NIST 800-53 to its Expanding Framework Library
Centraleyes announces the addition of NIST 800-53 to its extensive framework library. NIST 800-53 was created to…
Centraleyes Adds the HECVAT Risk Assessment to its Expanding Framework Library
Centraleyes announces the addition of the Higher Education Community Vendor Assessment Toolkit (HECVAT) its extensive framework library.…
A GRC Framework: 5 Tips for Building a Successful One
The GRC Revolution Unlike many catchphrases in the cyber dictionary, GRC (governance, risk, and compliance) is not…
Cyber Leaders of the World: Dan Wilkins, CISO at the State of Arizona
Please tell us a bit about yourself, your background, and your journey of becoming a CISO for…
Centraleyes Maps the FFIEC to its Expanding Control Inventory
Centraleyes announces the addition of the Federal Financial Institutions Inspection Council (FFIEC) to its expanding framework library.…
Inflation Impacts Cyber Data-Loss: Here’s What You Need to Know
Inflation is already impacting organizations worldwide, and its impact on the cost of cybersecurity incidents must be…
Cyber Data Loss: 4 Best Ways to Avoid
Data is the life force of business today. What would happen to a business if it was…
Everything You Need to Know About ESG Risk Assessment Tools
The way that your company conducts itself has never been more critical. Approximately 76% of consumers say…
Everything Startups Must Know About Compliance [Guide]
Most startups fail, so how can yours succeed? It’s a complex answer, but part of that answer…
New SEC Cybersecurity Reporting Requirements: Impact on Public Companies
The SEC Proposes New Cybersecurity Standards In March 2022, the SEC (Securities and Exchange Commission) released the…
Best Practices for Cyber Risk Quantification
The days of cybersecurity being a job exclusively for IT is over. In the past, data security…
The G in ESG: Why Governance Is So Important
The days of businesses thinking exclusively in terms of revenue are over. Now more than ever, companies…


















![Everything Startups Must Know About Compliance [Guide]](https://www.centraleyes.com/wp-content/uploads/2022/08/Blog_post_-_Everything_That_Startups_Must_Know_About_Compliance.jpg)




