Mourne Fourie
Mourne Fourie
An Introduction to the Hawaii Consumer Privacy Protection Act
Here’s an interesting fact about the Hawaii bill of rights: The Hawaii constitution lists the word “privacy”…
California Privacy Rights Act: What You Need to Know
Origins of the CPRA Mactaggart, a real estate developer in the California Bay Area, started worrying about…
What is Cybersecurity Risk Posture and Why Do I Need It?
“Stand straight.” It’s a directive we’ve all heard at some point in our lives and is worth…
What is the California Privacy Rights Act (CPRA)?
California has one of the strictest data protection legislation in the United States. CPRA deals with the…
Compliance Audit Trails: Why They're So Important
The growing body of stringent data privacy laws has pushed for better methods of evidence collection and…
Preparing for ISO 27002:2022 - What Do the Changes Mean for You?
What is ISO 27002:2022? Before we get started, let’s take a minute to explain exactly what ISO…
Cyber Risk Dashboard: The Metrics That Have Value for the Board of Directors
The Board Reporting Challenge Reporting the state of security at a board meeting can lead to confusion.…
Centraleyes Goes Live with Dedicated Risk Framework for Small Business Based on NIST 7621
Centraleyes announces the addition of NIST 7621 to its extensive framework library. The NIST 7621 framework provides…
The Importance of a Remote Access Policy
What Is a Remote Access Policy? As new digital waves continue to engulf the business landscape, remote…
Best Ways to Reduce Compliance Costs and Still Stay Compliant
The Third Digital Wave The digital transformation of the last few decades has completely changed the way…
Supply Chain Risk Management Explained
What is a Supply Chain? A supply chain is composed of multiple companies, vendors, and suppliers all…
Centraleyes Goes Live with the Latest Version of ISO 27001 2022 Standard
The ISO 27001 standard is internationally accepted as a specification for an Information Security Management System (ISMS).…
The Full NIST 800 53 Checklist: How to Prepare for an Audit
The NIST 800-53 Revision 5 provides a catalog of security and privacy controls for information systems and…
What is the NIST 7621 Cybersecurity Framework, and How Can it Help Small Businesses?
Cyber attacks and ransomware threats on small businesses may not reach the headlines, but they pose a…
Integrated Risk Management Software: A Complete Guide
Given the myriad of risks facing businesses today, business leaders are focusing on risk management like never…
Virginia Consumer Data Protection Act: The Most Important Things to Know About
Virginia Takes a Lead in Data Privacy Just eight pages long, the VCDPA is significantly more succinct…
Cyber Leaders of the World: Tony Velleca, CEO at CyberProof and CISO at UST
Please tell us a bit about yourself, your background, and your journey of becoming the CISO of…
Common Types of Network Security Attacks and How to Prevent Them in Your Enterprise
News outlets confirm what we don’t want to know. A single cyberattack can bring a sprawling corporate…
What is the Underlying Theory Behind the Zero Trust Security Model?
The Concept of Zero Trust In the past, companies focused security policies on controlling network perimeters, assuming…
Steps to Identify Controlled Unclassified Information and Protect It
What is Controlled Unclassified Information? CUI stands for Controlled Unclassified Information. CUI is defined as government-related information…
What's New in CIS Controls v8?
CIS Controls The Center for Internet Security (CIS), a non-profit organization with a mission to develop and…
Utah Consumer Privacy Act: What Do Businesses Need To Know
In the United States, most products are regulated by federal agencies that oversee safety standards and enforce…
Why Spreadsheets Don’t Work for Managing Risk Assessments
Microsoft Excel, Google Sheets, and their equivalent software programs are indispensable, and for good reason. These essential…
Colorado Privacy Act Signed Into Law: What You Need to Know
Privacy law is a trending topic in the United States. In the shadow of groundbreaking GDPR laws…
How To Perform a Successful GRC Gap Analysis
Gap analysis is a starting point for a business to compare its current state of information security…
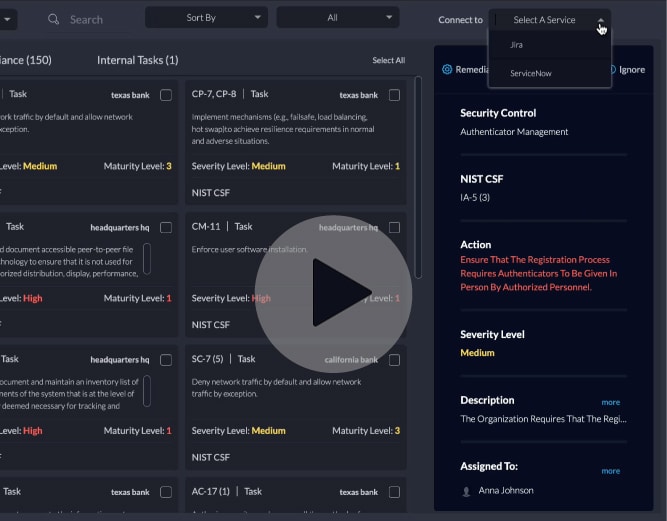
Enhance Your Cyber Maturity With ITSM Integration and Automated Remediation
Centraleyes makes your data actionable and enhances your cyber maturity by automatically creating remediation workflows whenever a…
How to Build a Successful GRC Program to Help Reduce Your Risk Posture
Watch this special, collaborated webinar session where Sagar Shah, Senior Manager of GRC at Corvus Insurance, and Yair Solow,…
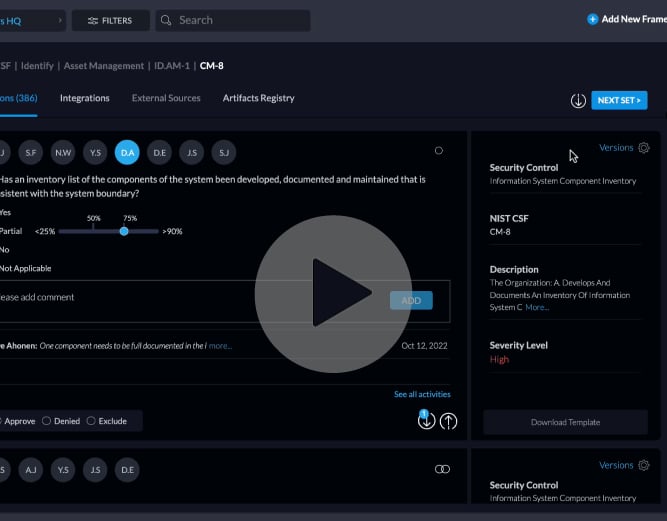
Ensure Your Ongoing Compliance With Automatic Framework Reassessment Tasks
Periodically reassessing your frameworks can be crucial to ensure your ongoing compliance and risk posture. With Centraleyes…
How to Manage Company Compliance During Recession: Complete Checklist
Since the 2008 recession, we’ve seen years of mostly low inflation, declining interest rates, and healthy stock…
New Data Privacy Law: Steps Organizations Should Take to Update Their Data Inventory for 2023
State legislatures across the US have been on a roll in introducing omnibus privacy bills. During the…