The Ultimate Cyber GRC Guide
In 1912, the Titanic set sail with the promise of being an unsinkable marvel. Yet, as history tragically unfolded, we saw a stark reminder of the consequences of overconfidence and overlooking critical risk factors.
The Titanic’s ill-fated voyage offers valuable insights into our modern business world. Archives harbor evidence of a deadly mix of low-quality material mixed with lofty ambition as the directors dreamed of crossing the Atlantic in record time. Let’s explore the striking parallels between the Titanic’s mistakes and how they relate to today’s organizations.


- The belief in being “too big to fail” clouded judgment and led to catastrophic consequences.
- Unchecked optimism in business decisions can be perilous.
- While the Titanic was compliant with the safety standards of its time, inadequate lifeboats demonstrated a glaring lack of insight into unforeseen circumstances.
- Modern organizations must ensure their risk management strategies encompass all possible scenarios.
- Flaws in the ship’s design and materials compromised its resilience, leading to devastating consequences. The Titanic’s rudder and propeller were too small for the ship’s massive size, and cheap materials were procured.
- Proper risk assessment is vital in determining strategic moves for cyber resilience.
- The board consistently ignored warnings about flaws in the construction of the ship.
- Regulatory oversight and governance are not just background noise. Their messages are meant to be incorporated into company culture.
In the pursuit of success, the Titanic made a fatal decision that ultimately sealed its fate.
Like the Titanic, modern businesses are intricate operations, complex and distributed. To navigate these complexities successfully, we require a robust risk management strategy. This strategy should encompass both the big picture and delve into the intricate details at the front line of the business.
Understanding the breadth and depth of GRC and cyber security risks is crucial, as it allows businesses to align risk management with strategic goals and objectives. Today, organizations require complete 360° situational awareness and risk visibility to achieve sustainable success. Enter the need for a holistic solution that enables organizations to reliably achieve objectives, address uncertainties, and act with integrity. In a nutshell, this is what lies at the foundation of GRC today.
Apply Cyber GRC to your organization today
Understanding GRC
What Is Governance, Risk, and Compliance?
GRC is an acronym for governance, risk and compliance that embodies a set of integrated functions that enable an organization to achieve objectives, address risks, and comply with regulated and self-imposed requirements.
To navigate the intricate risk landscape, businesses must establish a robust business model that addresses their obligations and ensures strategic oversight, risk management, and wholesome growth. By doing so, they lay the groundwork for success in an ever-evolving business environment.
To this end, the concept of GRC was codified by the OCEG, a grassroots organization, twenty years ago. They coined the acronym “GRC” and established a new approach to GRC management called “Principled Performance.”
GRC helps organizations experience a transformative journey, bridging the gaps between disconnected departments and evolving into a cohesive, integrated entity. This holistic approach empowers the organization to thrive unified and synergistically, fostering innovation, resilience, and sustainable success.
GRC, as per the OCEG, serves as the pathway to “Principled Performance.” It is not limited to being exclusively handled by the board or a particular compliance program. Instead, GRC involves the harmonious integration and orchestration of multiple capabilities. It acts as an umbrella, covering these core disciplines: governance, risk and compliance.
Breaking GRC Down To its Core Disciplines:
Governance
Refers to the rules, processes, and standards by which a business operates. In the context of GRC, governance involves establishing and enforcing controls, monitoring performance, and ensuring organizational activities align toward fulfilling business objectives and core values.
Risk
Risk management proactively identifies risks that may compromise crucial assets or impede strategic objectives and covers the path to remediation or mitigation.
Compliance
Compliance is typically viewed as ensuring an organization follows the rules and standards of regulatory agencies. However, aligning with the vision and values of the organization by keeping within voluntary boundaries is also included in the compliance function.
The Flow of GRC
The GRC acronym itself suggests a natural flow in its approach
2. Once this context is established, risk managers can project the uncertainties of achieving those objectives. Risk management also includes consideration of unexpected opportunities to leverage.
3. The compliance entity ensures the organization is on track with its objectives, risk strategy, and regulatory boundaries and provides “checks-and-balances” to the other two concepts.
A well-rounded GRC program has far-reaching effects on business strategy, sustainability, and security.
The Need For a New Approach to GRC in the Digital Age
In reality, GRC encompasses much more than its initials suggest. The fusion of the three concepts, and the way each branch interacts with the other two, is where the magic happens.
As businesses grow increasingly complex, they must effectively identify and manage critical organizational activities. Also required is the ability to integrate management activities into a cohesive discipline that increases the effectiveness of people, business processes, technology, and other essential business elements.
Modern GRC achieves this by breaking down the traditional barriers between business units and encouraging them to work collaboratively to achieve the company’s strategic goals.
An integrated GRC solution weaves risk management into the fabric of an organization. It relies on good communication between all departments to be successful.

Most importantly, GRC enables a “risk culture” that facilitates a more agile, forward-thinking process that beats the outdated compliance-driven approach to business strategy any day.
Most importantly, GRC enables a “risk culture” that facilitates a more agile, forward-thinking process that beats the outdated compliance-driven approach to business strategy any day.
Why Traditional GRC Methods Don’t Work Anymore
Exhaustive Manual Processe
Traditional GRC processes are manual and spreadsheet-based, which can result in lost time and human errors. Moreover, the lack of automation in traditional GRC methods results in inconsistent and error-prone operations that expose organizations to regulatory, compliance, and other risks.
Limited Visibility
Spreadsheet-based GRC methods offer little or no broad visibility into centralized data. This means that stakeholders may not have access to the information they need to assess and manage risks effectively.
In addition, one of the challenges facing compliance management teams is the sheer amount of data points for data collection and establishing control. An automated GRC platform delivers deep visibility into your corporate and vendor ecosystems, providing the information you need to make intelligent decisions.
Unnecessary Complexity
Complexity is a common pitfall in traditional GRC programs. Cumbersome processes, extensive paperwork, and manual data entry complicate risk management.
Fragmentation
Traditional GRC programs often fail to account for the cascading effects of risk. An isolated risk assessment may overlook potential impacts on interconnected systems, resulting in potential vulnerabilities being overlooked or underestimated.
Exponential Growth of Third-Party Relationships
Expanding supply chains and increased reliance on third-party vendors have changed the face of risk management. Third parties represent a risk if they do not promptly deliver their service or product. In addition, these relationships can expose your organization and make you liable for ethical or security lapses of third parties.
Clouds on the Horizon
Organizations are quickly adopting cloud computing, significantly impacting organizational structures, networks, attack surfaces, and access control mechanisms. New GRC solutions have adapted to this new paradigm, while traditional GRC methods still need to catch up.
The Benefits of an Automated GRC Program
An organization with the appropriate GRC components in place is one with an overall strategic plan that guides executive decision-making. Projects and initiatives are weighted and evaluated based on business-driven goals, risks are managed and measurable, and compliance burdens are known and communicated. Let’s examine the capabilities an automated GRC program can provide:
Cut out Redundancy
Silos of information are created where duplicate data and efforts overlap because each department operates independently.
In an automated GRC program, centralized data and clearly defined strategies cut out silos between departments to enable visibility and enterprise-wide collaboration. The ability to locate data and crosswalk that data to be used by various departments enables teams to work better together.
Risk Mitigation
Proactive risk assessment, mitigation techniques, developing an incident response strategy, and third-party vendor assessments all work to secure your enterprise and eliminate compliance-related fines and audit costs. Keeping a finger on the pulse of the ever-evolving threat landscape keeps your organization ahead of the game in the long run.
Operational Efficiency
Improved operational efficiency streamlines business processes in a compatible framework, paving the way to pursue new opportunities and markets confidently.
Automated Gap Remediation
An automated compliance system enables you to analyze compliance gaps easily. Once the gaps are identified, the platform will create automated actionable remediation tasks, guiding the team on what they need to do.
Visibility
Compliance and security teams can view their entire ecosystem, from internal servers to supply chain links.
Full visibility means control
Aggregating Data in a Centralized Location
When data is aggregated in a centralized repository, you sit on a gold mine of insights, which can strategically navigate you to identify weak domains, track your progress over time, and focus on the most critical elements of your organization.
Continuous Compliance Monitoring
As thorough as the spreadsheet or checklist of a traditional compliance check may be, it only captures a single point in time. Automated compliance platforms scan for vulnerabilities, notify you of changes to security frameworks, and offer risk remediation guidance based on real-time data. Robust risk management is nearly impossible without a continuous control monitoring system that uses automated tools.
The GRC Capability Model (by OCEG)
The GRC Capability Model serves as a structured framework that captures the evolving knowledge about how Governance, Risk, and Compliance function within an organization. It consists of four main components and twenty elements, enabling organizations to continuously address key questions and improve their GRC practices.
The model’s components and elements answer critical questions and facilitate governance, risk, and compliance conversations.
Learn
- Understanding the organization’s identity, its position, potential influences, stakeholders, and their expectations. It also involves examining the business model that guides the organization’s operations.
- Who are we?
- Who are our stakeholders?
- What is our current business model?
Align
- Defining the organization’s strategic direction, charting the path to achieve objectives, and addressing opportunities, challenges, and responsibilities that arise along the way.
- Where are we headed as an organization?
- How will we reach our goals and objectives?
- How will we address opportunities, obstacles, and obligations along the way?
Perform
- Evaluating the organization’s proactivity in risk management and its ability to identify issues, track progress, and effectively respond to favorable and unfavorable events.
- How proactive are we in managing risks?
- How do we detect problems and monitor progress?
- How do we respond to both favorable and unfavorable events?
Review
- Assessing the organization’s progress, evaluating the confidence level in GRC practices, and identifying areas for improvement.
- Are we making progress toward our objectives?
- How confident are we in our GRC practices?
- How can we improve our GRC capabilities?
Meeting Challenges Through GRC Technology
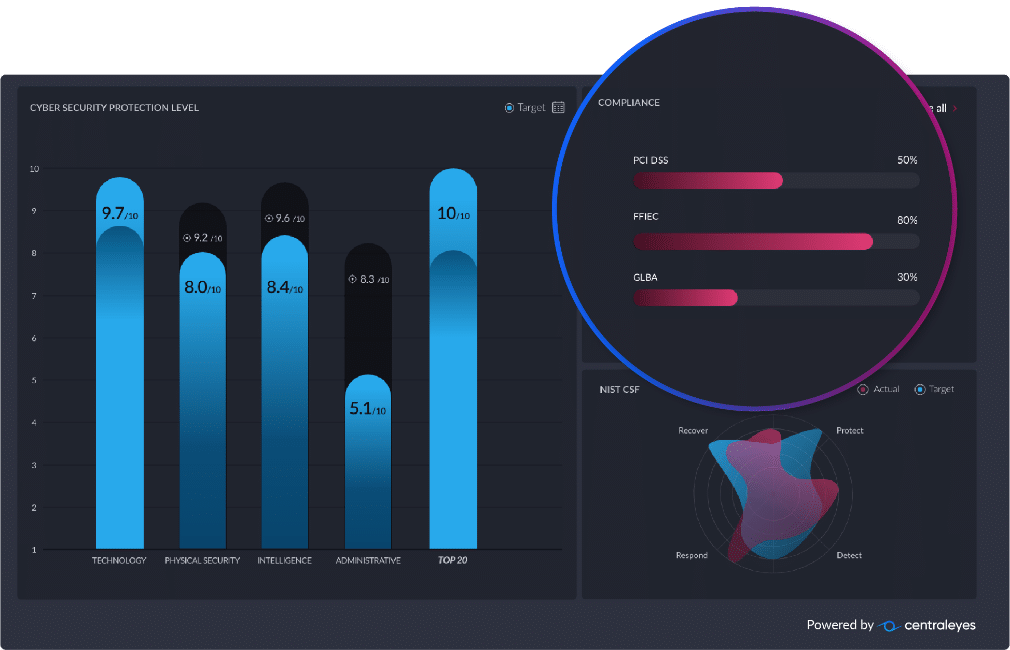
The emergence of automated GRC platforms like Centraleyes has created opportunities for organizations to tackle the all-too-well-known challenges of spreadsheet-based GRC. With new technologies on the market, organizations can enhance efficiency in terms of speed and cost reduction while fulfilling legal and security-related obligations and building a positive brand image.
Automated technologies can reduce the time employees are required to perform compliance tasks and shift the onus of risk management and compliance functions from tedious data

collection processes into more of an analytical role to decide whether to prioritize a given risk or which security control to implement.
With GRC no longer biased by human judgment but rather driven by relevant data or a strategic framework, the indispensable role of human talent can instead be channeled to analyze the assessment results based on real-time information. With such systems, decision-makers can dedicate their valuable time to planning that provides better value to the organization.
Apply Cyber GRC to your organization today
Implementing GRC
How to Successfully Implement a GRC Program in Your Company
1. Get Buy-in from Executive Leadership
Galvanize the top tier. As the ‘G’ in GRC suggests, senior management and board members must support the development of a GRC program before initiating the planning stages. When the executive suite is on your side and has allocated resources to a GRC program, you are well on the road to implementing a GRC framework.
The decision-making, risk management, and regulatory compliance functions included in a GRC framework will not be effective unless the organization’s executive leadership supports cultural change.
2. Define scope and Objectives
Choosing a GRC program isn’t too different than implementing any other IT system. Consider the size of your company, your most significant pain points, your budget, the complexity of deployment, and any other specific requirements you have. Look for a GRC platform that centralizes functions, processes, and workflows for optimum consistency, visibility, and communication between departments. Common goals include time-saving, eliminating dual labor, cost-effectiveness, and meeting compliance requirements.
- Are you concerned primarily with internal risk management, or do you want to meet a specific compliance or certification?
- Are you preparing for audits?
- Do you need to comply with multiple frameworks?
Keep these factors in mind as you establish the objectives of your GRC program.
3. Integrate and Orchestrate
You’ll need to integrate your GRC solution with the rest of your infrastructure, ensuring a seamless, uninterrupted data flow between them. This is crucial for the next, most important step: orchestration.
Orchestration refers to connecting security tools and integrating various loose ends of a security system into one tightly knit platform. It is a connection method that consolidates security functions and data collection, and it ultimately powers the next stage of modern GRC: automation for continuous and effective GRC management.
4. Choose a Framework
Selecting a GRC framework is a business decision rather than a technical choice. Take time to think about what actions your company “must do” and what “would be nice to do” to select an appropriate framework that doesn’t just help you avoid audit fines but protects your organization securely.
The more robust the framework, the more you can expect to have security and risk management in place for your company. Although it takes significant effort, it may be necessary to leverage a “meta-framework” like CSF or NIST cyber security framework to address controls and security requirements not mandated by law.
This process can be called “The Goldilocks Dilemma” of GRC in cyber security: “This framework is too tough, this one is too weak, this one seems to be just right!”
5. Perform a Gap Analysis
A gap analysis is a procedure that aids businesses in assessing how well their existing level of information security compares to particular standards or requirements. By doing a gap analysis, you will determine how far you are from the industry benchmark standards.
Who Should Be Involved in GRC Planning?
Cross-functional collaboration is crucial for effective governance, risk management, and regulatory compliance (GRC). Coordinating between various departments allows for a holistic approach to addressing risks and compliance issues, leading to better decision-making and reduced exposure to potential threats.
Senior executives are responsible for setting the organization’s strategic direction. When making critical decisions, they must assess potential risks and opportunities. They collaborate with risk management professionals to identify and evaluate risks associated with specific initiatives, investments, or market changes to achieve this. This collaboration ensures that risk considerations are integrated into decision-making, helping the organization make informed and risk-aware choices.

IT departments should be involved in the GRC planning stage, as well. They are vital in protecting the organization’s systems from cyber threats. They work closely with risk management and compliance teams to define the GRC role in cyber security strategies and protocols. This collaboration helps identify potential vulnerabilities, develop risk mitigation strategies, and establish incident response plans to address cybersecurity incidents promptly.
Choosing a GRC Solution
Consider a Risk-Based GRC Solution
GRC solutions often operate under the mantra “check the boxes and you’re safe.” They excel at helping organizations meet regulatory requirements, pass audits, and avoid penalties. Yet, compliance only sometimes equates to resilience, especially in the face of ever-evolving cyber threats and rapidly changing business landscapes.
Centraleyes recognizes that true GRC excellence goes beyond compliance checkboxes. It’s about understanding, assessing, and mitigating risks proactively. Here’s how Centraleyes is spearheading the cyber risk-based GRC revolution:
Risk at the Core
Centraleyes places risk front and center in GRC operations. Instead of treating compliance as the sole objective, it encourages organizations to identify, evaluate, and prioritize risks based on their potential impact and likelihood. This means that organizations can focus on what truly matters—protecting against threats that could harm their operations, reputation, and bottom line.
Today, being secure is more important than showing that you are secure.
Proactive Risk Mitigation
In the realm of GRC, being reactive is no longer sufficient. Centraleyes empowers organizations to take a proactive stance in managing risks. Rather than waiting for compliance violations or incidents to occur, organizations can implement preventative measures based on precise risk assessments. This approach minimizes the likelihood of costly breaches, incidents, or regulatory penalties.
Tailored Risk Assessments
Centraleyes allows organizations to conduct detailed and specialized cyber risk assessments. This includes identifying vulnerabilities, assessing the impact of potential cyber incidents, and evaluating the effectiveness of cybersecurity controls. It provides organizations with a comprehensive view of their cyber risk landscape.
Compliance with Risk Frameworks
Centraleyes assists organizations in ensuring compliance with cybersecurity regulations and standards. With the platform, you can easily navigate the complexities of data protection laws, industry-specific regulations, and risk frameworks, such as NIST and ISO 27001.
Resource Optimization
Centraleyes’ risk-based approach optimizes the allocation of resources. With a clear understanding of their risk landscape, organizations can channel resources toward the areas that pose the highest risk and reduce investment in lower-risk areas. This ensures that resources are used efficiently and effectively, making the most of available budgets.
So, when you’re faced with the choice between compliance-centric GRC solutions and Centraleyes’ risk-based approach, remember this: Compliance alone won’t shield you from the dynamic challenges of the GRC landscape. It’s time to embrace a more proactive, risk-centric path to GRC excellence, and Centraleyes is your trusted partner on that journey.
What to Look For When Choosing a GRC Solution
Smart Mapping
Smart mapping links compliance controls across multiple standards and frameworks. When you have confirmed your adherence to a security control in one framework, the same control is automatically confirmed across all the other frameworks and regulations. These mapped controls are rolled out seamlessly and automatically, making adherence to multiple regulatory or industry standards significantly more efficient.
Smart Remediation
When a compliance task is tagged as present or missing, automated smart remediation ensures that information is immediately shared across related tasks. This both improves organizational efficiency and eliminates unnecessary duplication of effort. When combined with smart mapping, smart remediation further helps break down complex frameworks into more digestible, manageable parts.
Real-Time Reporting
One of the most common GRC challenges is gathering all the information that auditors and regulatory bodies require to determine if you comply. Finding every piece of applicable data and creating reports is tedious and error-prone.
Instead, find a GRC platform that offers automated reporting. The right platform will generate the reports you need to give to auditors and regulators, with the click of a button, directly from your data collection. Additionally, you can create reports that provide decision-makers with actionable insights to help guide future decisions.
Advanced Risk-Management Tools
GRC and cybersecurity frameworks are heavily focused on creating risk scenarios. Risk scenarios describe threats and vulnerabilities that may enable a costly security incident. Preparing risk scenarios allows you and other decision-makers to implement controls to mitigate risks.
With the right platform, you can automatically build out risk scenarios. Many of the risks that face your business also face other businesses and have already occurred throughout your industry. An automated system can generate these risk scenarios based on historical data collected from multiple sources.
It’s worth noting that you will still need risk experts to review automated risk scenarios, and ideally, you may also need to use a combination of automated and manually created risk scenarios generated the old-fashioned way. Automated systems depend on historical data, and your organization may face a risk associated with a brand-new threat that will not yet have any available data. Yet, automatically generating risk scenarios can save significant time and free up security experts to focus on high-impact tasks.
Evidence Collection and Logging Capabilities
GRC programs require evidence and a lot of it. Every certification and legal regulation will need proof to prove that you comply. Evidence can range from documented policies and procedures, information about implemented risk-mitigating controls, or raw data regarding a specific aspect of your business.
Don’t let evidence collection take up any more of your employees’ time and energy. Instead, free them up to work on more important tasks and reduce the error-prone nature of manual evidence collection.
You’ll need the right GRC platform that makes evidence collection a straightforward and automated task. Automated evidence collection is a vital aspect of creating a scalable GRC program.
Comprehensive reporting is essential to GRC, as it allows organizations to track progress, identify gaps, and communicate outcomes to stakeholders. Well-structured reports provide valuable insights into the effectiveness of risk management strategies and compliance efforts.
Third (and fourth!) Party Vendor Management
Just as important as managing your internal risks, Vendor security risk management is included in the GRC umbrella. Thankfully, you don’t have to start from scratch, handle calculations manually, and pour through compliance documentation with every vendor when you leverage a platform that simplifies and automates vendor risk management without sacrificing accuracy or effectiveness.
Scalability for Future Requirements
Your organization doesn’t need to implement GRC initiatives for\ every department simultaneously. If you want to boost compliance but worry about the budget, start small and scale up gradually.
Falling back on your risk-based priorities, focus on your most important GRC initiatives and go down the list in order of importance. Again, integrated GRC platforms allow you to scale your framework as you grow.
Get started on Your GRC Journey with Centraleyes
With Centraleyes’ automated GRC platform, you can perform risk assessments and build relevant metrics to compile a comprehensive analysis of GRC requirements for your company. With tens of pre-populated integrated risk and compliance frameworks that map and share controls, Centraleyes allows for quicker, automated compliance and security processes.
Our platform is scalable and can be advanced as security needs evolve. It includes integrated risk assessment tools, strong reporting and analytics capabilities, and third-party vendor assessments. Most importantly, it allows for customization beyond industry-standard regulatory requirements of risk management.
At Centraleyes, we’ve built our solution on the presumption that a siloed approach to GRC is cumbersome and that an integrated risk management solution is the best way forward.
Planning, assessing, monitoring, and reporting have never been easier with our centralized, integrated platform.
The Centraleyes solution cuts across organizational silos. It breaks down and overcomes the barriers or divisions between different departments or units within an organization. This is achieved by establishing common and standardized definitions and classifications for risks and controls and enabling users to coordinate and unify risk management activities across all business functions.