Yehuda Raz
Yehuda Raz
Top Benefits of Effective 3rd Party Vendor Risk Management
Today’s businesses don’t operate in a vacuum. To maintain high standards of efficiency, supply chains everywhere need…
4 Critical Capabilities Your Cyber Risk Management Tools Should Have
Cybersecurity is top of mind for most businesses today. A single data breach can compromise your ability…
CMMC v2.0 vs NIST 800-171: Understanding the Differences
The U.S. Defense Industrial Base (DIB) Sector is the worldwide industrial complex that enables research and development,…
The SOC 2 Compliance Checklist for 2024
SOC 2 is the gold standard in Information Security certifications and shows the world just how seriously…
Top Cybersecurity & Third-Party Risk Management Trends to Follow in 2024
The aftershocks of the disruption created by the coronavirus will be felt for years to come. Almost…
Everything You Need To Know About The New York Privacy Act 2021
Finding a balance between the need to handle personal information and protecting the privacy of individuals can…
Preparing for your SOC 2 Audit - Do’s and Don’ts
Legend has it that SOC 2 is one of the most challenging audits out there, achievable only…
Everything You Need to Know About UK Cyber Essentials
What is UK Cyber Essentials? Cyber Essentials is a government-backed scheme that was created to help organisations…
What Is SOC 2 Automation Software and Why It's Necessary
In its quest to specify how organizations should manage their customers’ data, the American Institute of CPAs…
The Best of Both Worlds: Why Modern Risk Management Demands a Hybrid Approach
An ounce of prevention is worth a pound of cure. Decision-makers would do well to remember this.…
How to Integrate an ESG Framework into Your Risk Management Plan
Every aspect of a business is affected by ESG from its very inception through to production and…
Benefits of Automating SOC 2 Compliance and Why Is It Important?
Achieving a gold medal has always involved stamina, perseverance, hard work and determination. Achieving this gold-standard compliance…
How Automating Audit Workflows Streamlines the Process
Every audit will involve an official inspection and thorough examination of your company: its IT systems, networks,…
What is the Massachusetts Data Privacy Law (MIPSA)?
Unlike Europe and its GDPR (General Data Privacy Regulation), the United States doesn’t have a blanket set…
What Are the Elements of an Effective GRC Program?
The landscape of risks and threats your business now faces is more complex than it’s ever been.…
ESG Risk Management: How to Conduct Risk Assessments, Analyze and Prioritize
As far back as the early 1900s, special laws and government agencies were beginning to pop up…
How IT Risk Management Impacts Your Organization
No business is without risk — and anyone who believes otherwise is due for a rude awakening. …
Why Every Business Needs a Cybersecurity Incident Response Plan
Imagine if you knew someone was about to break into your house. With adequate time to prepare,…
Why Board Members Should care about ESG Compliance Software
Environmental, Social and Governance (ESG) issues are a regular part of mainstream consciousness and are continuously gaining…
How to Implement a Vulnerability Management Program — and Why You Need One
Between the shift to distributed work, the growth of the Internet of Things, and the troubling surge…
How Do You Choose a GRC Platform for Your Company
Every great company has a sound business plan. It encompasses knowledge and expertise, evaluates the market, calculates…
What Does Compliance Automation Enable for Your Business?
Compliance has long been a thorn in the side of IT departments — not in the least…
GRC vs. IRM: A New Approach to Risk Management
The Internet of Things is growing at a breakneck pace, with the total number of connected devices…
How To Develop a Cybersecurity Risk Management Plan
Cybercrime is on the rise in virtually every industry. Today’s businesses are facing an unprecedented threat landscape…
How Insurance Companies Can Leverage Cyber Risk Management
Last year set multiple records for cyber crime, and none of them were good. DDoS attacks soared…
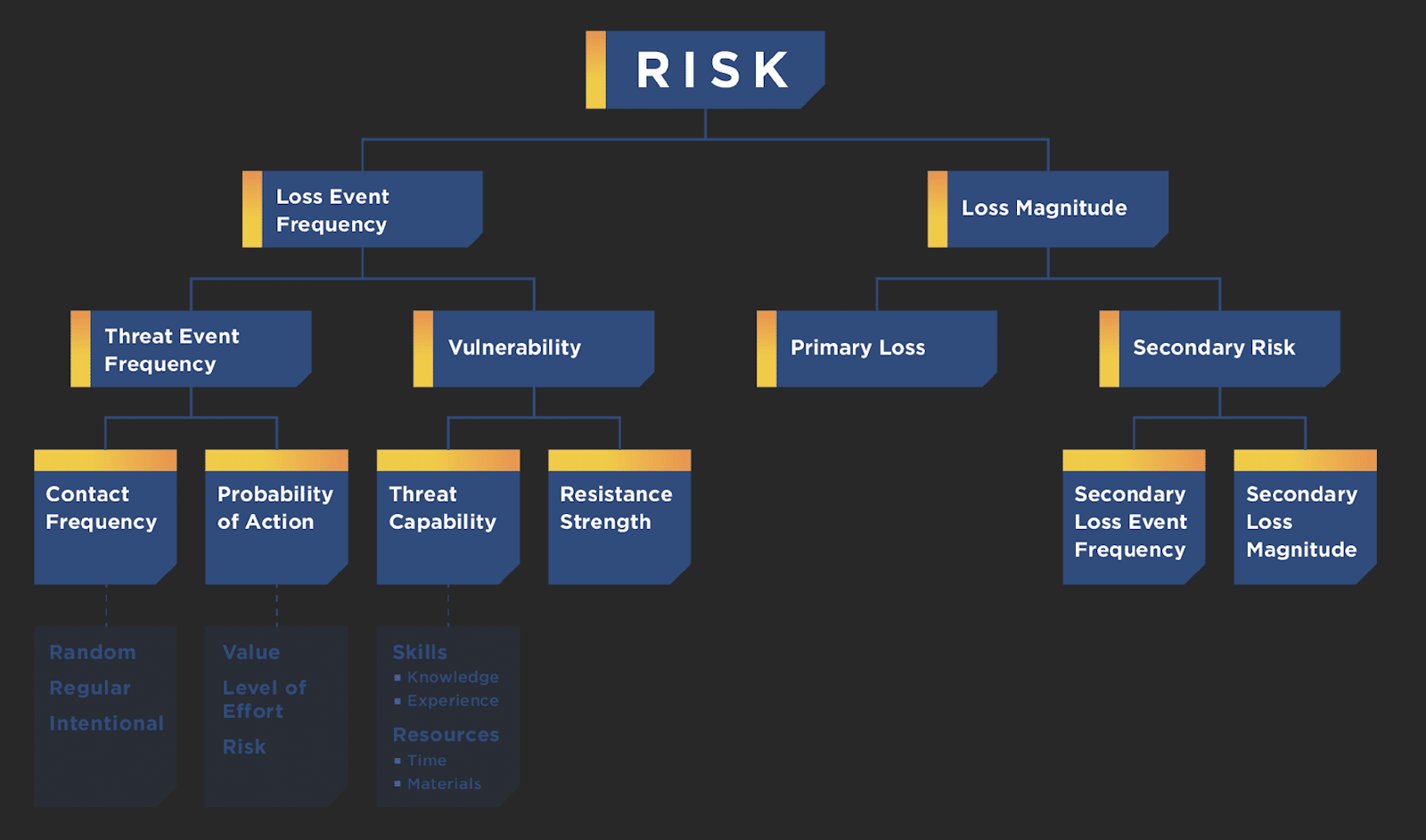
FAIR Model Risk Management - Pros and Cons
Information risk is not just a technical problem but affects the bottom line and daily activities of…
How To Create an Effective Vendor Management Program
Vendors are an essential component of your organization and many times now a true extension of your…
Top 5 Cybersecurity Tips for Your Organization During the Holidays
The holiday season gives malicious actors the perfect opportunity to attack your organization’s systems to obtain sensitive…
M&A Cybersecurity Due Diligence Best Practices: What You Need to Know
Mergers and acquisitions (M&A) are intended to boost the value of your brand or business when you…
Cyber Risk Management For Investment Portfolios: Why Private Equity Firms Should Pay Attention
The goal of any investment is to generate a positive return on that investment—so that part’s obvious.…