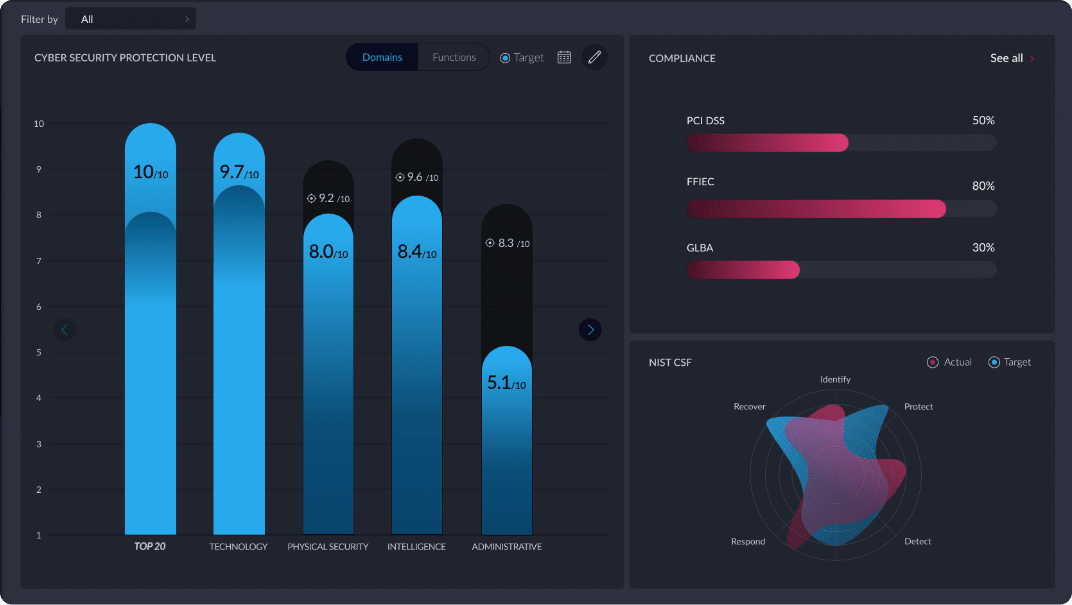
NIST CSF
- Home
- NIST CSF
NIST CSF
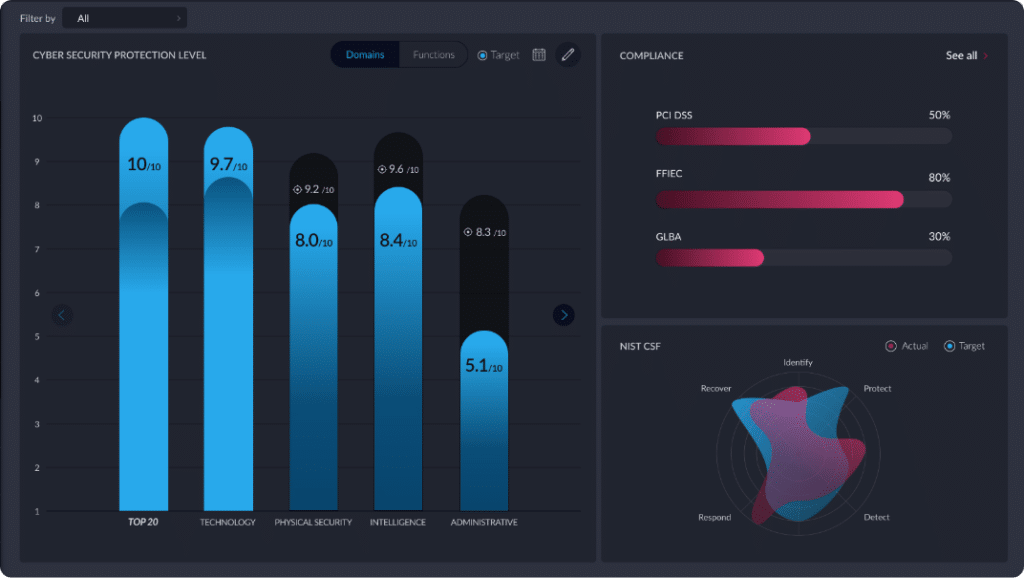
The NIST CSF presents a high-level collection of guidelines, standards and practices used to organize and improve your cybersecurity program, as well as prevent, detect and respond to cyberattacks



NIST has done all of the hard work for us, creating easy to understand guidelines in a clear precise language. Centraleyes is here to help you get these cyber frameworks implemented. Our experts have put together this helpful guide to navigate NIST – learn what it offers, how to use it and who it is suited for. Make sure to click on the links throughout the article to gain a deeper understanding of any topic
Background to NIST Standards
With a world-wide shift to cloud hosting and online services, a company’s critical infrastructure needs to be well guarded more than ever before. While a physical location is accessible only to those in the vicinity, anything hosted online can be potentially accessible to anyone, anywhere in the world. Every day the news is full of ransomware attacks, data breaches and companies struggling to protect critical infrastructure. Keeping sensitive data safe from breaches, systems free from attacks and business operations uninterrupted can seem an overwhelming task
NIST, the National Institute of Standards and Technology, is a government agency with a mission to boost U.S. innovation and industrial competitiveness by producing guidelines that will enhance economic security, boost productivity and keep up standards across the US. One of NIST’s most important functions is to provide structure and context to cybersecurity. Read more about the NIST institute at the end of this article

Cybersecurity involves highly specialized knowledge yet a basic (and often deeper) understanding of the topic is essential to every organization across every industry. Appointing a CISO (Chief Information Security Officer) or hiring dedicated cyber risk management specialists is becoming the norm, but not every organization will have the budget to do so. Therefore, clear cybersecurity information with practical applications needs to be available in an easy to understand format in order to succeed in protecting the masses.
And this is what NIST provides

What Is the NIST
Cybersecurity Framework?
This framework provides a common language and set of best practices for managing cybersecurity risks. It is designed to be flexible and adaptable, and can be used by organizations of all sizes and types.
The foundational cybersecurity framework established by NIST is their NIST CSF. Based on current principles, protocols and procedures, the NIST CSF boosts cybersecurity for any size organization by providing a framework to evaluate their cyber posture and enhance their capacity to avoid, track and react to cyber incidents. Adhering to the NIST CSF guidelines reduces an organization’s cyber risk, boosts and strengthens the company’s cybersecurity postur.e



The NIST CSF, which was published in 2014 by executive order of President Barack Obama and updated in 2018, has grown to be an essential tool for risk management for both public and private sector organizations. A 2017 executive order mandates NIST CSF compliance for federal government agencies and the companies that make up their supply chains.
Complying with the NIST CSF is entirely voluntary (unless you are a federal agency or aiming for a government contract), yet so is locking your front door at night. When you consider the exorbitant costs of a data breach, ransomware attack or any kind of disruption to business operations, complying with NIST CSF becomes a wise move
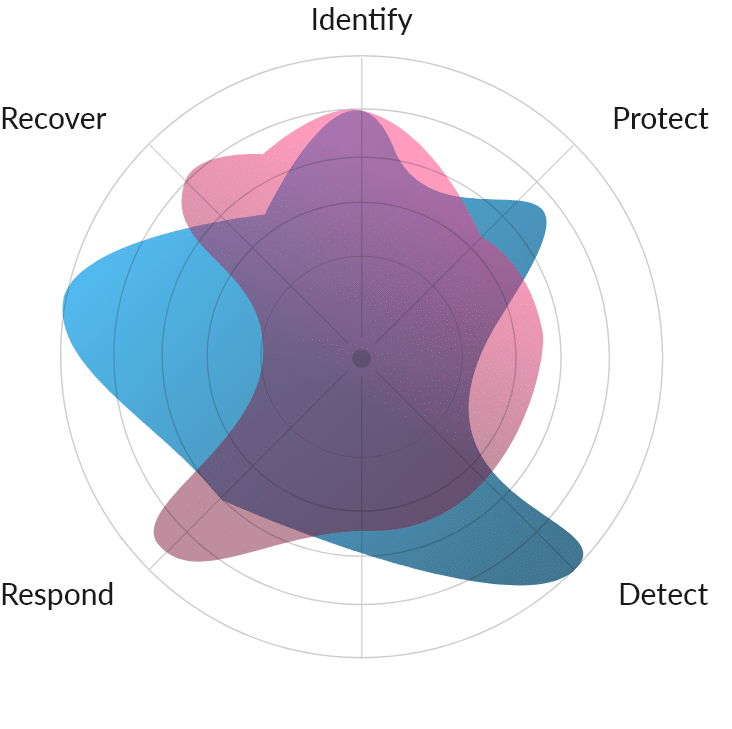
The 5 NIST Functions
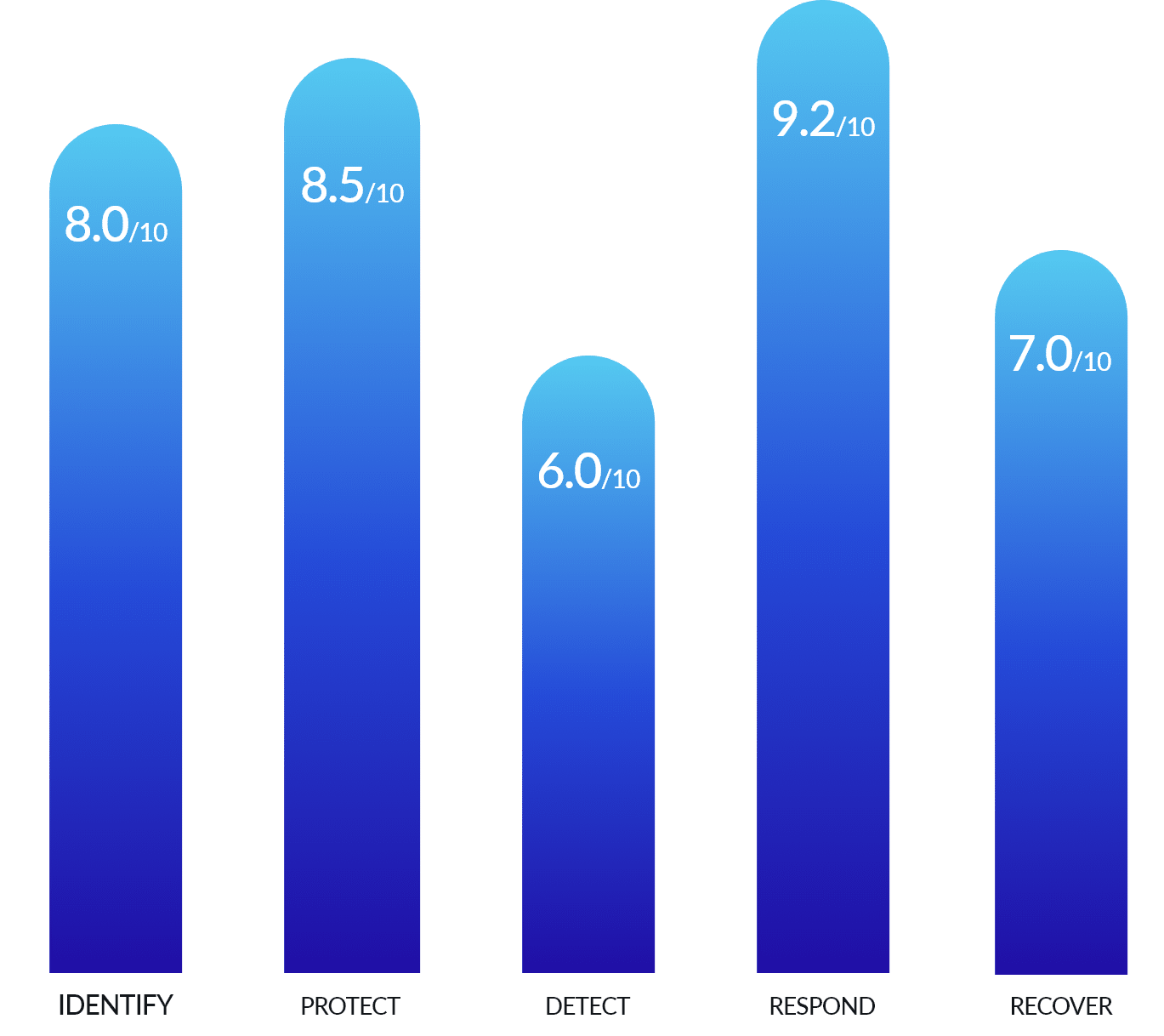
Apply the NIST 5 Pillars to your organization today
What Are the NIST Framework Core Components?
The following are the three primary components of NIST CSF:
Framework Core
The Core offers systematic cybersecurity practices to use as a roadmap for organizations to handle their cybersecurity threats in a way that complements current cyber and risk management processes
Framework Implementation Tiers
The Tiers help organizations determine the required degree of rigor for their cybersecurity program and set the stage for how a company can approach cyber risk management. Tiers are often used as a means of communicating about threats and budget
Framework Profiles
The Profiles align the organizational requirements and objectives, risk appetite and resources against the desired outcomes of the Framework Core. Profiles are primarily used to identify and prioritize opportunities for improving cyber resilience at an organization
A Variety of NIST Publications
NIST CSF is the broadest and most widely used framework, due to its compatibility with most organizations, yet, there are industries dealing with extra sensitive information, or whose impact or severity are critically high. These cyber situations call for more specialized guidelines and controls and NIST provides for those as well
Amongst the publications, these are the most commonly used:
As you’d expect, the government is pretty protective over their systems and requires all their contractors to adhere to the same level of security. These 1000+ controls are requirements for federal agencies who work with government systems to protect against potential security issues and cyber attacks. This publication provides guidelines for securing federal information systems and organizations.
NIST SP 800-53A – This publication provides guidelines for assessing the security controls in federal information systems and organizations.
The way people work has changed dramatically with a high rise in those working from home, remotely accessing company systems. Mobile devices and flexible working conditions also mean that more employees than ever are bringing their own devices to work. NIST has created a set of guidelines and technical specifications named “Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security”.
Read more about securing your enterprise while working-from-home with NIST 800-46.
In the fast-paced world of producing innovative products that use our personal information to tailor the user experience, guarding privacy is a challenge of its own. The NIST privacy framework provides privacy protection strategies, privacy risk management concepts, and information about how the NIST CSF can be applied to privacy risk.
NIST created recommendations for Industrial Controls Systems (ICS). It provides “an overview of ICS and typical system topologies, identifies typical threats and vulnerabilities to these systems, and provides recommended security countermeasures to mitigate the associated risks”. It also takes into consideration Supervisory Control and Data Acquisition (SCADA) systems, Distributed Control Systems (DCS), and other control system configurations such as Programmable Logic Controllers (PLC).
The NIST Zero Trust moves the focus away from network location and concentrates on protecting resources like assets, services, workflows and network accounts. The document is a set of cybersecurity principles used when planning and implementing an enterprise architecture, on the basis that verification is always necessary! “Never trust, always verify.”
Read more about achieving zero-trust.
This publication provides guidance on protecting controlled unclassified information (CUI) in nonfederal information systems and organizations. This is usually used in companion with the 800-53 documentation. It covers the requirements of dealing with Controlled Unclassified Information (CUI) for contractors and subcontractors of federal government agencies. Keep in mind that the U.S. Department of Defense’s “CMMC” (Cybersecurity Maturity Model Certification), required for DoD contractors, is based in part on NIST 800-171.
A Sample of Other NIST Frameworks
The National Institute of Standards and Technology (NIST) has published a number of cybersecurity frameworks and guidelines to help organizations protect their systems and data that are lesser known. These frameworks are not intended to be competitive with one another, but rather to provide guidance and best practices for different types of organizations and use cases. Here is a list of 6 other NIST cybersecurity frameworks:
NIST Small Business Cybersecurity Act (SBCA)
This framework is designed specifically for small businesses, and provides guidance on how to identify and mitigate cybersecurity risks
NIST SP 800-82
This publication provides guidance on securing industrial control systems (ICS), including those used in
critical infrastructure
NIST SP 800-137
This publication provides guidelines for implementing a cybersecurity incident
response program
NIST SP 800-160
This publication provides guidance
on systems engineering
for cybersecurity
NIST SP 800-161
This publication provides guidelines for securing the internet of things (IoT)
NIST SP 800-163
This publication provides guidelines for securing cloud computing environments
Learn more about which NIST publications are relevant to your organization
What is the difference between ISO 27001 and NIST?
The ISO 27001 and NIST standards are both Information Security Management System (ISMS) standards that focus on the security of information. They serve different purposes though, with NIST providing a framework for effectively managing individual risks and ISO 27001 providing a template for how an organization should build its system for protecting sensitive data and information. To learn more about how these two standards compare, dive into our article on the topic
ISO 27001
Is a standard that governs security management and its implementation. ISO 27001 specifies information security objectives, controls and management processes. This standard also includes an organizational requirement for risk assessment and business impact analysis, as well as a framework of implementing these controls.
NIST 800-171
is an implementation of ISO 27001, but it is not completely aligned with the standard. NIST 800-171 is less prescriptive than ISO 27001, allowing organizations to have more flexibility in their security program design and implementation.
ISO 27001 VS. NIST
The most significant difference between NIST and ISO 27001 is that the NIST standard offers different objectives and controls, while the ISO standard is based on a maturity model where the various levels of a company’s security are closely related to one another. In addition, while the NIST standard is working towards CSF 2.0, the last revision came in 2014, ISO 27001 was updated more recently in 2022
How To Get Started With NIST Cybersecurity Framework
The following principles are immensely helpful in implementing NIST CSF and you can decide what suits your organization. With that said, it is highly recommended to use an automated
Risk and Compliance Platform that will eliminate the guesswork, provide you with the tools to sail through all of these steps, and prepare you for future risk and compliance frameworks
IDENTIFY
Begin with a comprehensive risk assessment and use it to identify everything within the scope. What needs protection? What are your assets? Take inventory. Decide what is within the scope. Not just hardware, software and equipment, but also roles and responsibilities. Who has access to sensitive data? Map it, scope it, identify all relevant systems, data flows, assets and more. Now you know what you’re working with, it is time to protect.
PROTECT
This is where your security controls come into play. Work through the NIST controls. Manage who accesses your network and who makes use of your PCs and other equipment. Deploy security software. Secure sensitive data both in transit and at rest. Make regular data backups. Regularly update security software, and if you can, automate those updates. Have explicit protocols in place for disposing of outdated technology and electronic files responsibly. Teach cybersecurity to everyone who uses your network, computers and other devices. Employees can benefit from understanding their own personal risk as well as their critical job responsibilities.
DETECT
Set up tools to monitor your networks, any access points, review logs, set up alerts and ensure any unusual activity is spotted and investigated on an ongoing basis! Follow the NIST CSF to develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
RESPOND
A significant part of building a robust cybersecurity plan is being ready to respond to a cyber incident. In the words of Benjamin Franklin, “By failing to prepare, you are preparing to fail.” Follow the NIST CSF as you create a plan that includes notifying customers, employees and others whose data may be at risk. A business continuity plan should focus on keeping business operations up and running. Be ready to report the attack to law enforcement and other authorities. Prepare for investigating and containing an attack. Following an incident, update your cybersecurity policy and plan with lessons learned. Cyber attacks are not the only type of incidents that may have an impact on your security and operations. Prepare for inadvertent events (like weather emergencies) that may put data at risk.
RECOVER
NIST put it the best. Use the Recover function to develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event. Thinking and preparing ahead for how to get back on your feet following any negative incident.
Get started with a FREE NIST assessment today
NIST Maturity levels: NIST CSF
Maturity Levels of NIST CSF Framework: The information security maturity levels refer to the process through which organizations may move in order to enhance their security. These are the core concepts that identify the various stages of an organization’s information security environment. The framework defines five levels of maturity that can be achieved by implementing effective security measures and technical solutions, executive management support and employee participation.
Maturity level 1
Partial
Maturity level 2
Risk-Informed
Maturity level 3
Repeatable
Maturity level 4
Adaptable
The pillar page of the NIST CSF (Cybersecurity Framework) was created to help guide organizations and teams as they move through maturity levels in their adoption of the NIST Cybersecurity Framework.
The NIST Cybersecurity Framework is a set of standards and guidelines for implementing, managing and monitoring cybersecurity programs in an organization. Maturity Levels define the characteristics that are needed to achieve success within each phase. As an organization achieves higher maturity levels, it becomes more effective at addressing cybersecurity needs.
The maturity levels are intended to be used as a guide toward improving cybersecurity risk management (CRM) practices and capabilities, with the goal of enhancing an organization’s ability to manage cybersecurity risk effectively. These maturity levels apply to phases along the cyber value chain, from strategic planning through continuous monitoring, including those cybersecurity capabilities essential to effectively protect organizational assets from cyber exploits and cyber threats.
NIST makes clear that the CSF Implementation Tiers are not designed to be a maturity model.
They are designed to highlight and give guidance to how cybersecurity risk management and operational risk management processes interact.
Why comply with NIST? What is NIST Compliance?
We’ve mentioned above government related situations where compliance with certain NIST publications is required, but besides those, there is no sweeping legal requirement to comply with NIST specifically. There are, on the other hand, many legal requirements to implement certain controls and take certain precautions, many of which are covered by the NIST guidelines.
So while NIST guidelines may not be obligatory, you may be otherwise obligated to implement all of the controls listed in those guidelines
The obvious advantage of adhering to NIST guidelines is the protection it offers from threat actors and cyber incidents, namely DDoS attacks, ransomware, data breaches and others. With the current slew of ransomware attacks, NIST protection is more valuable than ever before.
Aligning security controls, procedures, policies and processes with NIST is the foundation to preparing for all the other compliance and risk frameworks. For example, those who must comply with FISMA (Federal Information Security Management Act) have already met the prerequisite standards by complying with NIST. Both HIPAA (Health Insurance Portability and Accountability Act) and SOX (Sarbanes-Oxley Act) also require the foundational security controls that NIST puts in place.
Another advantage is protecting your organization’s eligibility to bid for government contracts or work with federal agencies. In some cases, noncompliance or failure to maintain NIST will result in a loss of work, breach of contract, reputational harm or even legal liability.
The safety NIST provides is a clear advantage.
Learn more about which NIST publications are relevant to your organization
Building your NIST CSF Cyber Risk Management
Program With Centraleyes
Centraleyes has incorporated NIST CSF to develop a comprehensive platform to building a cyber risk management program. Centraleyes helps you meet these challenges with NIST Cybersecurity Framework
Centraleyes provides secure cloud hosting for NIST Cybersecurity Framework adherence, along with full visibility and analysis into your organization’s compliance program. This end-to-end solution allows your team to focus on your business goals, while Centraleyes eases your entire risk and compliance management process. A pillar-based approach to cyber risk management allows you to apply NIST standards and policies in a systematic way.
The Centraleyes platform is built on NIST CSF, incorporating all of the controls, tracking coverage of the 5 functions, and smart mapping it to a multitude of other risk and compliance frameworks. All of the main NIST publications are built-in to the platform, making it a smooth and simple process to align your organization with their requirements. With our support, detailed descriptions and automated remediation steps, we provide all the tools you need to succeed in your journey to align with NIST.
NIST Recent and Upcoming updates
NIST is primarily concerned with building the security of our infrastructure and making sure that we are compliant with the best practices. The recent updates include NIST 800-181, which provides a way to protect Personally Identifiable Information (PII) in IoT devices. NIST has also defined the baseline standards for cyber-physical systems and sensors, including Cloud computing security guidance, which was published in September 2018.
Recent updates to NIST are the current standards that have been completed in the review and approval process. The upcoming standards will begin their review and approval process after they have been published.
NIST is a non-profit institute that develops standards and guidelines for many industries, including the information security industry. NIST has developed the following standards for key generation, elliptic curve cryptography, and the introduction of quantum computers.
New standards are constantly evolving and being adopted, or discontinued. For example, the previous version of NIST SP 800-128 has reached its end-of-life and is no longer available. The current version of NIST SP 800-128 has been updated with a new publication date, but remains unchanged from the previous version.
Learn More About NIST
CMMC v2.0 vs NIST 800-171: Understanding the Differences
What Is NIST Zero Trust Architecture & How to Achieve It
NIST 800-46: Securing Your Enterprise in the Work-From-Home Reality
NIST Privacy Framework – The Next Generation of Enterprise Privacy Has Arrived
Understanding the NIST Institute and NIST Assessments
NIST is an agency of the U.S. Department of Commerce that conducts research and provides technical assistance in a variety of areas, including information technology, engineering, and physical sciences. As part of its mission, NIST conducts assessments in various fields to identify and evaluate emerging technologies, assess the state of existing technologies, and provide recommendations for improvement.
NIST assessments are typically carried out by teams of experts in the relevant field, who may be NIST employees or contractors. The specific number of assessments conducted by NIST each year can vary, as the agency’s work is dictated by the needs and priorities of the various industries and agencies it serves.
NIST assessments may be conducted in response to a request from a government agency, industry organization, or other stakeholder, or they may be initiated by NIST based on the agency’s own research and development priorities. The scope and focus of an assessment may vary widely, depending on the needs and goals of the project. Some assessments may be narrow in focus, examining a specific technology or issue in detail, while others may be more broad, examining a range of technologies or issues within a particular field or industry.
NIST assessments typically involve a comprehensive review of the relevant literature and data, as well as interviews with experts and stakeholders. The assessment team may also conduct experiments or demonstrations to test the performance of technologies or evaluate their suitability for a particular application. Based on the results of the assessment, the team may provide recommendations for improving the technology or addressing any identified issues or challenges.
NIST conducts a variety of assessments each year in a range of fields, including information technology, engineering, and physical sciences. These assessments are carried out by teams of experts and involve a comprehensive review of the relevant literature and data, as well as experiments or demonstrations to test the performance of technologies. The results of NIST assessments are highly respected and are often used by government agencies, industry organizations, and other stakeholders to inform their decision-making processes and guide the development of new technologies and policies.
The National Institute of Standards and Technology (NIST) is the U.S. government agency that creates standards, guidelines, test methods, reference materials, and technologies in a broad range of measurements, computing systems, geometries and materials used in the nation’s economy. It is an integral part of the U.S. federal government’s system of innovation and technology transfer which includes partnerships with universities and industry that work together to create new products, processes and services through technological innovation.
NIST collaborates closely with other national laboratories and technology centers engaged in similar research and development efforts to ensure that the United States remains a global leader in science and technology, especially measurement standards development.
NIST (National Institute of Standards and Technology) is a non-regulatory federal agency that promotes U.S. innovation, industrial competitiveness and economic growth. NIST develops scientific and technical standards, tests, and practical guidelines to serve diverse interests within industry, federal agencies, and the public.
NIST has two centers within its organization, one for Information Technology (IT) security and one for biotechnology. The National Cybersecurity Center of Excellence (NCCoE) was created in 2010 as an expansion of the National Initiative for Cybersecurity Education (NICE) to provide leadership across the entire cybersecurity discipline and incorporate additional information technology sectors into its scope. It is interesting to note that the term cybercrime was not coined by NIST or any other Government agency, but was introduced by a French demographer named Jacques-Lucien Marchand in 1895.






